Annual Audit Manual
COPYRIGHT NOTICE — This document is intended for internal use. It cannot be distributed to or reproduced by third parties without prior written permission from the Copyright Coordinator for the Office of the Auditor General of Canada. This includes email, fax, mail and hand delivery, or use of any other method of distribution or reproduction. CPA Canada Handbook sections and excerpts are reproduced herein for your non-commercial use with the permission of The Chartered Professional Accountants of Canada (“CPA Canada”). These may not be modified, copied or distributed in any form as this would infringe CPA Canada’s copyright. Reproduced, with permission, from the CPA Canada Handbook, The Chartered Professional Accountants of Canada, Toronto, Canada.
5035.3 Segregation of duties
Sep-2022
In This Section
Purpose of segregation of duties
Roles and responsibility assignments
Information technology general controls
Segregation of duties versus restricted access
Management override of controls
Evaluation of segregation of duties
Use of automated tools and techniques for segregation of duties
OAG Guidance
In order for internal controls to be effective, there needs to be an adequate division of responsibilities among those who perform accounting procedures or controls and those who review such activities. Ideally, the flow of transaction processing and related activities are designed so that the work of one individual is either independent of, or serves as a check on, the work of another.
Segregation of duties:
-
reduces the risk of undetected error and limits opportunities to misappropriate assets or conceal intentional misstatements in the financial statements, and
-
serves as a deterrent to fraud or concealment of error because of the need to recruit another individual’s cooperation (collusion) to conceal it.
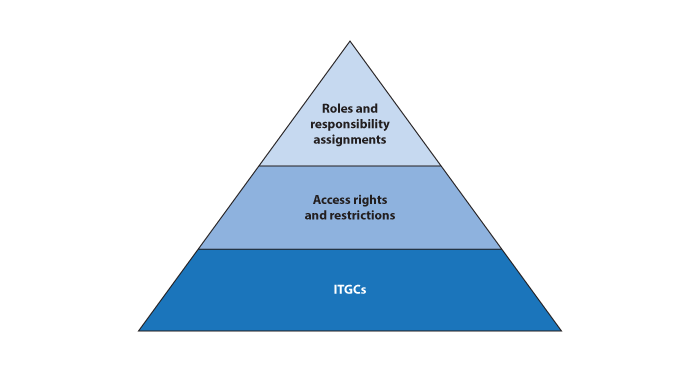
Segregation of duties is accomplished by the proper assignment of roles and responsibilities, enabled by appropriate access rights and restrictions built into the system, and supported by Information technology general controls (ITGCs) over system access rights and restrictions. The below diagram depicts the importance of these different layers, with ITGCs being the foundation. Controls at each layer need to be designed, implemented and operating effectively to enable reliance on segregation of duties.
OAG Guidance
Proper division of responsibilities generally consists of assigning different people to
- authorizing transactions,
- performing controls related to recording and processing transactions,
- monitoring those controls,
- maintaining accounting records, and
- having physical access or custody of assets or key records/documents.
Examples:
-
To reduce the risk of error, management may establish procedures for the review and approval of monthly reconciliations of a control account by a supervisory level employee who does not perform the reconciliations.
-
To reduce the risk of fraud, responsibilities for the shipping and billing functions are ordinarily segregated to prevent unauthorized shipment of goods from being concealed by circumventing the usual billing procedures.
-
Developers that create or update changes to the IT environment do not have access to make or move changes into the production IT environment. Having the ability to develop and implement changes in the production environment might allow for circumvention of key automated information processing controls or direct manipulation of financial transactions and data.
-
To help prevent unauthorized changes, 'super user' access is granted only to a limited number of users within the IT department and the system logs of their activities are monitored on a periodic basis by the chief information security officer (CISO).
Access to the production environment is controlled using Firefighter access controls. Firefighter access controls mean that access to change or update the production environment is provided only for authorized changes that have been tested and approved in the test environment. There are restrictions over which users are granted this access and there is a time limit set. The logs of changes are reviewed as part of change management control
OAG Guidance
The ability to achieve effective segregation of duties is enhanced by implementing proper controls over access to the information system (including programs, databases, operating system and network), important documents or entity assets. Such access is restricted to authorized individuals commensurate with the duties assigned to them in the design of internal control. Often controls over access rights are subject to our design and implementation evaluation and our operating effectiveness tests, including ITGC test results. We consider the results of this access testing to obtain evidence over the entity’s segregation of duties controls.
Physical controls are commonly needed for restricting physical access to negotiable assets such as cash or securities or for inventory or other items that might easily be converted to cash or personal use. These controls are often reviewed through observation and inquiry procedures.
Examples:
-
The design of controls over sales transactions may necessitate the segregation of billing and shipping duties, but the desired level of control may not be achieved if an individual responsible for processing shipping transactions also has the ability, through inappropriate user access rights, to process billing transactions on the system.
-
The design of controls over cost of sales may require physical custody of inventory to be segregated from other inventory processing and accounting responsibilities, but the desired level of control may not be achieved if inventory is easily accessible to individuals other than those charged with custodial responsibility.
Establishing appropriate access rights and restrictions also contributes to the achievement of the restricted access information processing objective.
Related Guidance
See OAG Audit 5035.4 for further guidance on information processing objectives.
OAG Guidance
Guidance addressing Information technology general controls (ITGCs) to support segregation of duties is included in OAG Audit 5035.2.
OAG Guidance
Segregation of duties is different from restricted access. Restricted access, an information processing objective, protects data against unauthorized access; however, it does not provide information regarding individual responsibilities for authorizing transactions, recording transactions, and maintaining custody of assets. Segregation of duties is part of the foundation of internal control to achieve the validity and restricted access information processing objectives for each component of the entity’s system of internal controls.
OAG Guidance
Due to diversity in entity sizes, systems, types of operations, and a host of other variables, there is no one set of segregation of duties controls that can be used. Variety is to be expected, and the effectiveness of segregation of duties controls will depend on unique circumstances and risks. It is not uncommon for entities to combine functions or duties that would ideally be segregated where the risks of combining them are sufficiently low or are otherwise mitigated. Points that may be considered when determining whether to segregate duties include
- the volume, complexity and financial significance of different types of transactions;
- the sequence of steps necessary to process transactions;
- the technology and application system(s) used to process transactions;
- the opportunities or motives for individuals to commit fraud or perpetuate errors;
- the risk of loss or financial misstatement due to errors or fraud; and
- the existence of alternative or compensating controls.
Based on the analysis performed we may conclude there is a lower risk of incompatible duties as alternative or compensating controls exist. In such situations document the rationale for why the lack of segregation of duties does not present the potential for fraud or management override and how the alternative control reduces the risk of material misstatement.
For example, an organization that provides on-site warranty services via field technicians driving trucks containing spare parts may hold the technicians responsible for: maintaining custody of the inventory; recording inventory usage via handheld wireless data input devices; and directly purchasing and replenishing the inventory. While it may seem less than ideal to combine such duties for any one individual, determining whether the combination creates an internal control deficiency requires further consideration of the risk of material misstatement to the financial statements due to error or fraud, such as:
-
How material is the inventory to the financial statements, and how vulnerable is the inventory to misuse or theft based on its nature and value to others?
-
Is the risk of fraud and error spread among a very large number of independent service technicians or is it concentrated in a few?
-
Are there alternative or compensating controls such as periodic physical inventory counts performed by internal audit or regional supervisors or other independent parties?
-
Is there effective monitoring, such as the accounting department performing an analysis of inventory balances and usage against sales and warranty data, where territories or technicians with anomalous results are identified and investigated?
OAG Guidance
The impact and potential for management override of internal controls on the audit depend to a great extent on the integrity, attitude, and motives of the individual. As in any other audit, exercise professional skepticism and neither assume that the individual is dishonest nor assume unquestioned honesty. Management override is an important factor to be considered when assessing audit risk, planning the nature and extent of audit work, evaluating audit evidence, and assessing the reliability of management representations.
As discussed in OAG Audit 5506, procedures to address the risk of management override are performed on every audit, including
- examining journal entries and other adjustments,
- reviewing accounting estimates for biases, and
- evaluating the business rationale for significant unusual transactions.
OAG Guidance
The level of work performed over segregation of duties depends on the planned audit approach and assessment of risks. First, it is important to obtain a sufficient understanding of the internal control components, including control activities, to assess the risks of material misstatement at the assertion level and to design further audit procedures responsive to the assessed risks. An audit does not require an understanding of all controls, but we focus on understanding controls in areas where material misstatements due to errors or fraud are more likely to occur (see additional guidance in OAG Audit 5035.1 for futher guidance in identification of controls that address risk of material misstatement). Segregation of duties may or may not be relevant to that analysis during planning, depending on the assessment of risks and the nature of the client’s approach to mitigating fraud risk.
When evaluating segregation of duties a risk based approach may be considered for significant business processes. Below are proposed procedures that may be considered in an audit where reliance is expected to be placed on segregation of duties as a control.
If segregation of duties is important to mitigating significant risks identified at the assertion level, then at a minimum we need to evaluate the related controls, which means that most of the procedures described below (particularly the first four) would ordinarily be performed to some extent as part of planning the audit. This is true regardless of the ultimate decision to place reliance on controls. Throughout the audit process be aware of new or heightened risks of fraud or error based on the results of our work, and evaluate the impact on our planned audit approach. If segregation of duties is determined to be as a relevant control, we would add this control as a process wide control. When performing any of these procedures, consider the skills and experience needed to perform the procedure and check that proper resources such as IT audit or fraud risk specialists are appropriately involved.
When evaluating segregation of duties we employ the following 6 steps:Step 1—Understand the company’s system of internal control and related assignment of functional duties.
An understanding over the components of the entity’s system of internal control is important in evaluating the effectiveness of segregation of duties.
A further understanding is obtained at the information processing level when reliance on controls is planned or whenever properly assigned and segregated duties are important for evaluating the components of the entity’s system of internal controls. Judging whether duties need to be segregated to properly mitigate the risks of fraud or error will take into account the particular circumstances of the client. It is not uncommon for organizations to combine functions or duties that would ideally be segregated where the risks of combining them are sufficiently low or are otherwise mitigated. Consequently, we evaluate the need for segregation of duties in light of circumstances that may vary widely from entity to entity.
Step 2—Obtain evidence that duties are actually being carried out in accordance with individuals’ assigned roles and responsibilities.
It is important to obtain first hand evidence, not only that roles and responsibilities are properly assigned (Step 1), but also that they have been implemented. Procedures to obtain such evidence as part of understanding and evaluating controls might include targeted inquiry of individuals with varying duties and responsibilities throughout the transactions cycle combined with direct observation of their respective activities.
Step 3—Understand the entity’s approach for defining and assigning an individual’s rights to access systems, programs, data, documents or assets. Evaluate whether system and physical access rights are appropriately assigned to achieve effective control design.
Gain an understanding of management’s approach to security and evaluate how management’s establishment of access rights and restrictions supports segregation of duties. This step can be technically challenging, depending on the complexity of the entity’s systems / processes and the entity’s approach to managing system security (e.g., by transactions, by role, by the person). Note that inappropriate access rights and restrictions do not just affect segregation of duties. Delegation of authority and information processing objectives may also be adversely affected. For example, access to a sensitive transaction such as the ability to update vendor master file records may be granted to an excessive number of individuals without commensurate duties or authority. Understand ITGCs and related monitoring activities and evaluate whether they are properly designed to preserve the ongoing integrity and appropriateness of access rights and restrictions. Also refer to OAG Audit 4028 for ITGCs guidance.
Step 4—Test the operating effectiveness of ITGCs and monitoring controls.
This step is necessary if we plan to place reliance on ITGCs and/or monitoring controls. Refer to OAG Audit 5035.2 for guidance related to ITGCs.
Step 5—Obtain evidence that system and physical access rights are actually granted to and/or restricted from individuals in accordance with their assigned access rights and restrictions.
It is important to obtain first hand evidence, not only that access rights are properly assigned in the design of controls (Step 3), but also that such rights have actually been granted to, or restricted from, personnel according to that plan. This step is generally performed as of a point in time and is suggested as the last step because the nature, timing and extent of our work can vary depending on the results of work performed in all the prior steps. Examples:
-
If our work on relevant ITGCs shows that the process for granting application user access rights is ineffective, we may not want to test actual access rights at all. On the other hand, doing a limited test of access rights early in the audit might help to corroborate a preliminary assessment of significant risks surrounding security and access controls.
-
If our assessment based on the above procedures is that the entity has an effective combination of preventive and detective controls and a long, validated history of little or no issues related to the establishment of system access rights and restrictions, then we may be able to reduce the nature and extent of work needed to test actual system access rights and restrictions based on our understanding, evaluation and testing of the ITGCs and related monitoring activities. For example, we might be able to limit our testing of actual access rights and restrictions to a sampling of higher risk transaction types or users, rather than a more extensive testing of perhaps all users’ rights and restrictions.
It is likely that most entity environments will require some combination of preventive and detective controls to maintain appropriate day-to-day access rights and restrictions. The required frequency of monitoring will vary depending upon the risks and effectiveness of preventive controls. Any exceptions identified in this test of access rights would also be evaluated to consider what impact those results may have regarding our conclusion on the overall effectiveness of ITGCs.
Step 6—Evaluate and respond to segregation of duties deficiencies.
If reliance was planned on segregation of duties as a selected control and deficiencies are noted within the segregation of duties controls, we document the deficiency and evaluate the severity and the impact of the deficiency on our audit approach. In evaluating the impact on our audit approach we consider the following:
-
The risks associated with the incompatible duties.
-
Whether management has implemented alternative controls that would effectively mitigate the risks that we can test for operating effectiveness.
-
Substantive procedures that are planned that will address the risks associated with incompatible duties.
-
Additional substantive procedures that may be necessary to address the risk related to the financial assertion(s) impacted by the incompatible duties.
Impact of Other Internal Control Components
In evaluating the design effectiveness of segregation of duties controls, consider other internal control components as follows:
| Internal control components | Considerations |
|---|---|
| Control environment | Does management establish an organization structure that considers key areas of authority and responsibility, establishes appropriate lines of reporting, and defines the framework for delegating and limiting authority commensurate with responsibilities? |
| The entity’s risk assessment process | Does management consider the risk of error or fraud due to lack of appropriate segregation of duties or inappropriate access rights that could result in material misstatement of the financial statements? |
| Information and communications | Does management clearly communicate roles and responsibilities and function duties in a manner that supports the relevant internal control objectives? |
| The entity’s process to monitor the system of internal control | Does management monitor the controls over access rights and restrictions to verify they remain appropriate over time? Such monitoring activities might include:
|
OAG Guidance
Automated tools exist for a few of the more common ERP systems and technical platforms which can be used to assist in validating actual access rights assigned within the client’s systems. Management may use similar tools to facilitate their assessment. If we plan to leverage the use of tools by management, consider both the tool itself (as an automated control) and the manual controls surrounding use of the tool. Consider the effectiveness and reliability of management’s tool and its output through an evaluation of the system logic and/or our own independent testing.
OAG Guidance
Guidance addressing segregation of duties in less complex entities is included in OAG Audit 5035.6.