Annual Audit Manual
COPYRIGHT NOTICE — This document is intended for internal use. It cannot be distributed to or reproduced by third parties without prior written permission from the Copyright Coordinator for the Office of the Auditor General of Canada. This includes email, fax, mail and hand delivery, or use of any other method of distribution or reproduction. CPA Canada Handbook sections and excerpts are reproduced herein for your non-commercial use with the permission of The Chartered Professional Accountants of Canada (“CPA Canada”). These may not be modified, copied or distributed in any form as this would infringe CPA Canada’s copyright. Reproduced, with permission, from the CPA Canada Handbook, The Chartered Professional Accountants of Canada, Toronto, Canada.
5035.2 Identify the risks arising from the use of IT and the related ITGCs
Sep-2022
In This Section
Identify IT applications and other aspects of the IT environment
Identify risks arising from the use of IT
Identify entity’s ITGCs that address risks arising from the use of IT
OAG Guidance
As part of understanding and evaluating the entity’s system of internal control, we obtain or update our understanding of how the entity uses information technology (IT) relevant to the preparation of the financial statements and how the entity responds to risks arising from the use of IT. Refer to OAG Audit 5034 for further guidance on understanding the IT environment relevant to the information system.
It is only after understanding how the IT environment is relevant to the preparation of the financial statements that we fully understand the entity’s processes, data flows and risks, including risks arising from the use of IT. The following are examples of some factors that can influence an entity’s need to use IT:
- The type of business (e.g., entity that develops digital property which requires sophisticated IT infrastructure to protect)
- Business model (e.g., online sales, subscription business)
- Compliance with laws or regulations (e.g., data protection laws or electronic filing requirements of regulators)
- Financial reporting risks identified by the entity as part of its operations that can be mitigated with the use of technology (e.g., automated calculations to minimize manual errors)
Why is this important?
It is through the identification of IT applications and other aspects of the IT environment (e.g., databases, operating system, network) relevant to the preparation of the financial statements that engagement teams are able to identify the risks arising from the use of IT and related information technology general controls (ITGCs) that address these risks. This provides the basis for the engagement team to understand the entity, identify and assess risks of material misstatements, assess the control risk as documented by our determination of expected controls reliance (i.e., none, partial or high), and develop effective and efficient audit responses to address the risks of material misstatement.
Therefore, even though we may later decide not to test the operating effectiveness of ITGCs or other controls, the risks which these controls are designed to address will need to be understood as part of our risk assessment and considered when developing our responses to risks of material misstatement. For example, the entity may manage its customer accounts receivable using an IT application (the “accounts receivable subledger” which automatically interfaces with the revenue collection application used to match revenue against invoice) because there is a large volume of revenue and collection transactions and management concluded it is more effective than managing it manually using a spreadsheet application such as Microsoft Excel. Management implements ITGCs and other information processing controls aimed at ensuring accurate processing and to maintain the integrity of the information reflected in the accounts receivable subledger. Regardless of any plan to test the operating effectiveness of controls addressing relevant assertions of the accounts receivable FSLI, there are risks arising from the use of this IT application, such as the risk that unauthorized or untested changes, or the failure to make necessary changes to application configuration when generating a system‑generated report such as an accounts receivable aging report, could result in transaction records not being processed completely and accurately. We consider this risk as part of our risk assessment process even if we only intend to make use of the report for substantive testing purpose. If we plan to use the report as part of a test of controls or for our substantive procedures, we still need to address the completeness and accuracy of the source data, (which in this example is the data received via the interface with the revenue collection application, therefore we may need to consider the interface as an IT dependency and the report logic.
Within the block below Identify risks arising from the use of IT, we address, in more detail, the identification of IT risks and in the block below Identify entity’s ITGCs that address risks arising from the use of IT we cover identifying ITGCs to address those risks, which together comprise the “Identify IT risks and ITGCs” element of the OAG Risk Assessment Process illustrated below.
Identifying risks arising from the entity’s use of IT and the entity’s ITGCs that address such risks
The following chart shows how we utilize the understanding of the various elements of an entity’s system of internal control to identify risks arising from the entity’s use of IT and the entity’s ITGCs implemented to address those risks:
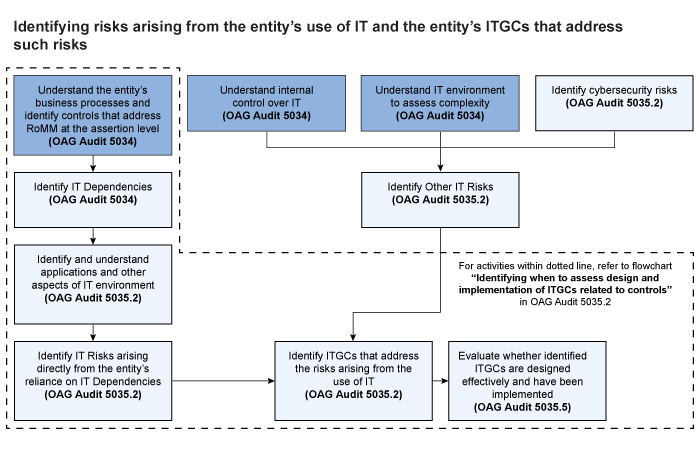
Mapping CAS 315 terminology to OAG Audit
General Information Technology Controls
CAS 315 refers to General Information Technology Controls. This is equivalent to the term Information Technology General Controls (ITGCs) used in OAG Audit.
ITGC Domains
CAS 315 provides relevant requirements addressing the need to understand the entity’s internal controls and emphasizes the importance of obtaining an appropriate understanding of the IT environment. Although the ITGC domain names used in OAG Audit have not been updated to align to the revised ITGC domain names used in CAS 315 (Revised), the meaning of the terms are the same and related procedures designed to assess the design and test the operation of ITGCs relevant to the network, operating system or database layers, fully align with the requirements and guidance of the revised standard. These domain names used in OAG Audit may be updated in the future to eliminate the narrowing terms such as “program” or “program and data”. For now, the following table provides a mapping of the ITGC domain names used in OAG Audit to those used in CAS 315:
| OAG Audit ITGC Domain Name | CAS 315 ITGC Domain name | Comments |
|---|---|---|
| Access to Programs and Data | Manage access | The Access to Programs and Data ITGC domain is used to consider access to the IT environment. This aligns with the CAS 315 Manage Access process, including access to applications (including application programs), databases (including data), operating system and the network |
| Program Change | Manage Change | The Program Change ITGC domain is used to consider changes to the IT environment. This aligns with the CAS 315 Manage Change process, including the process to manage program or other changes to the IT environment (excluding the “Systems development or acquisition or implementation” and “Data conversion” elements – see Program Development below) |
| Program Development* | Manage Change | The Program Development ITGC domain is used to consider larger scale changes, e.g., new IT applications or other aspects of IT developed, configured and implemented in the period. This aligns with the CAS 315 Manage Change process, including the process to manage programs or other changes to the IT environment and including the “Systems development or acquisition or implementation” and “Data conversion” elements. |
| Computer Operations | Manage IT Operations | The Computer Operations ITGC domain is used to consider ongoing management of IT operations, including job scheduling and monitoring, backup and recovery and intrusion detection. This aligns with the CAS 315 Manage IT operations process. |
*CAS 315 references three IT Processes—Manage Access, Manage Change and Manage IT Operations. OAG Audit guidance includes a fourth domain “Program Development” to enable us to more easily identify and focus on development related activities at the entity and the related audit work. Equally, if the entity does not undertake development in the period, this ITGC domain would not need to be evaluated, which helps facilitate effective and efficient working practices.
CAS Requirements
The auditor shall obtain an understanding of the control activities component, through performing risk assessment procedures, by (CAS 315.26):
(b) Based on controls identified in (a), identifying the IT applications and the other aspects of the entity’s IT environment that are subject to risks arising from the use of IT;
CAS Guidance
Understanding the risks arising from the use of IT and the general IT controls implemented by the entity to address those risks may affect (CAS 315.A166):
- The auditor’s decision about whether to test the operating effectiveness of controls to address risks of material misstatement at the assertion level;
Example: When general IT controls are not designed effectively or appropriately implemented to address risks arising from the use of IT (e.g., controls do not appropriately prevent or detect unauthorized program changes or unauthorized access to IT applications), this may affect the auditor’s decision to rely on automated controls within the affected IT applications.
- The auditor’s assessment of control risk at the assertion level;
Example: The ongoing operating effectiveness of an information processing control may depend on certain general IT controls that prevent or detect unauthorized program changes to the IT information processing control (i.e., program change controls over the related IT application). In such circumstances, the expected operating effectiveness (or lack thereof) of the general IT control may affect the auditor’s assessment of control risk (e.g., control risk may be higher when such general IT controls are expected to be ineffective or if the auditor does not plan to test the general IT controls).
- The auditor’s strategy for testing information produced by the entity that is produced by or involves information from the entity’s IT applications;
Example: When information produced by the entity to be used as audit evidence is produced by IT applications, the auditor may determine to test controls over system‑generated reports, including identification and testing of the general IT controls that address risks of inappropriate or unauthorized program changes or direct data changes to the reports.
- The auditor’s assessment of inherent risk at the assertion level; or
Example: When there are significant or extensive programming changes to an IT application to address new or revised reporting requirements of the applicable financial reporting framework, this may be an indicator of the complexity of the new requirements and their effect on the entity’s financial statements. When such extensive programming or data changes occur, the IT application is also likely to be subject to risks arising from the use of IT.
- The design of further audit procedures.
Example: If information processing controls depend on general IT controls, the auditor may determine to test the operating effectiveness of the general IT controls, which will then require the design of tests of controls for such general IT controls. If, in the same circumstances, the auditor determines not to test the operating effectiveness of the general IT controls, or the general IT controls are expected to be ineffective, the related risks arising from the use of IT may need to be addressed through the design of substantive procedures. However, the risks arising from the use of IT may not be able to be addressed when such risks relate to risks for which substantive procedures alone do not provide sufficient appropriate audit evidence. In such circumstances, the auditor may need to consider the implications for the audit opinion.
For the IT applications relevant to the information system, understanding the nature and complexity of the specific IT processes and general IT controls that the entity has in place may assist the auditor in determining which IT applications the entity is relying upon to accurately process and maintain the integrity of information in the entity’s information system. Such IT applications may be subject to risks arising from the use of IT (CAS 315.A167).
Identifying the IT applications that are subject to risks arising from the use of IT involves taking into account controls identified by the auditor because such controls may involve the use of IT or rely on IT. The auditor may focus on whether an IT application includes automated controls that management is relying on and that the auditor has identified, including controls that address risks for which substantive procedures alone do not provide sufficient appropriate audit evidence. The auditor may also consider how information is stored and processed in the information system relating to significant classes of transactions, account balances and disclosures and whether management is relying on general IT controls to maintain the integrity of that information (CAS 315.A168).
The controls identified by the auditor may depend on system‑generated reports, in which case the IT applications that produce those reports may be subject to risks arising from the use of IT. In other cases, the auditor may not plan to rely on controls over the system‑generated reports and plan to directly test the inputs and outputs of such reports, in which case the auditor may not identify the related IT applications as being subject to risks arising from IT (CAS 315.A169).
The extent of the auditor’s understanding of the IT process, including the extent to which the entity has general IT controls in place, will vary with the nature and the circumstances of the entity and its IT environment, as well as based on the nature and extent of controls identified by the auditor. The number of IT applications that are subject to risks arising from the use of IT also will vary based on these factors (CAS 315.A170).
Examples:
-
An entity that uses commercial software and does not have access to the source code to make any program changes is unlikely to have a process for program changes, but may have a process or procedures to configure the software (e.g., the chart of accounts, reporting parameters or thresholds). In addition, the entity may have a process or procedures to manage access to the application (e.g., a designated individual with administrative access to the commercial software). In such circumstances, the entity is unlikely to have or need formalized general IT controls.
-
In contrast, a larger entity may rely on IT to a great extent and the IT environment may involve multiple IT applications and the IT processes to manage the IT environment may be complex (e.g., a dedicated IT department exists that develops and implements program changes and manages access rights), including that the entity has implemented formalized general IT controls over its IT processes.
-
When management is not relying on automated controls or general IT controls to process transactions or maintain the data, and the auditor has not identified any automated controls or other information processing controls (or any that depend on general IT controls), the auditor may plan to directly test any information produced by the entity involving IT and may not identify any IT applications that are subject to risks arising from the use of IT.
-
When management relies on an IT application to process or maintain data and the volume of data is significant, and management relies upon the IT application to perform automated controls that the auditor has also identified, the IT application is likely to be subject to risks arising from the use of IT.
When an entity has greater complexity in its IT environment, identifying the IT applications and other aspects of the IT environment, determining the related risks arising from the use of IT, and identifying general IT controls is likely to require the involvement of team members with specialized skills in IT. Such involvement is likely to be essential, and may need to be extensive, for complex IT environments (CAS 315.A171).
The other aspects of the IT environment that may be subject to risks arising from the use of IT include the network, operating system and databases, and, in certain circumstances, interfaces between IT applications. Other aspects of the IT environment are generally not identified when the auditor does not identify IT applications that are subject to risks arising from the use of IT. When the auditor has identified IT applications that are subject to risks arising from IT, other aspects of the IT environment (e.g., database, operating system, network) are likely to be identified because such aspects support and interact with the identified IT applications (CAS 315.A172).
Through understanding the nature and complexity of the entity’s IT environment, including the nature and extent of information processing controls, the auditor may determine which IT applications the entity is relying upon to accurately process and maintain the integrity of financial information. The identification of IT applications on which the entity relies may affect the auditor’s decision to test the automated controls within such IT applications, assuming that such automated controls address identified risks of material misstatement. Conversely, if the entity is not relying on an IT application, the automated controls within such IT application are unlikely to be appropriate or sufficiently precise for purposes of operating effectiveness tests. Automated controls that may be identified in accordance with paragraph 26(b) may include, for example, automated calculations or input, processing and output controls, such as a three‑way match of a purchase order, vendor shipping document, and vendor invoice. When automated controls are identified by the auditor and the auditor determines through the understanding of the IT environment that the entity is relying on the IT application that includes those automated controls, it may be more likely for the auditor to identify the IT application as one that is subject to risks arising from the use of IT (CAS 315 Appendix 5.8).
In considering whether the IT applications for which the auditor has identified automated controls are subject to risks arising from the use of IT, the auditor is likely to consider whether, and the extent to which, the entity may have access to source code that enables management to make program changes to such controls or the IT applications. The extent to which the entity makes program or configuration changes and the extent to which the IT processes over such changes are formalized may also be relevant considerations. The auditor is also likely to consider the risk of inappropriate access or changes to data (CAS 315 Appendix 5.9).
System‑generated reports that the auditor may intend to use as audit evidence may include, for example, a trade receivable aging report or an inventory valuation report. For such reports, the auditor may obtain audit evidence about the completeness and accuracy of the reports by substantively testing the inputs and outputs of the report. In other cases, the auditor may plan to test the operating effectiveness of the controls over the preparation and maintenance of the report, in which case the IT application from which it is produced is likely to be subject to risks arising from the use of IT. In addition to testing the completeness and accuracy of the report, the auditor may plan to test the operating effectiveness of general IT controls that address risks related to inappropriate or unauthorized program changes to, or data changes in, the report (CAS 315 Appendix 5.10).
Some IT applications may include report‑writing functionality within them while some entities may also utilize separate report‑writing applications (i.e., report‑writers). In such cases, the auditor may need to determine the sources of system‑generated reports (i.e., the application that prepares the report and the data sources used by the report) to determine the IT applications subject to risks arising from the use of IT (CAS 315 Appendix 5.11).
The data sources used by IT applications may be databases that, for example, can only be accessed through the IT application or by IT personnel with database administration privileges. In other cases, the data source may be a data warehouse that may itself be considered to be an IT application subject to risks arising from the use of IT (CAS 315 Appendix 5.12).
The auditor may have identified a risk for which substantive procedures alone are not sufficient because of the entity’s use of highly‑automated and paperless processing of transactions, which may involve multiple integrated IT applications. In such circumstances, the controls identified by the auditor are likely to include automated controls. Further, the entity may be relying on general IT controls to maintain the integrity of the transactions processed and other information used in processing. In such cases, the IT applications involved in the processing and the storage of the information are likely subject to risks arising from the use of IT (CAS 315 Appendix 5.13).
The entity’s ability to maintain the integrity of information stored and processed in the information system may vary based on the complexity and volume of the related transactions and other information. The greater the complexity and volume of data that supports a significant class of transactions, account balance or disclosure, the less likely it may become for the entity to maintain integrity of that information through information processing controls alone (e.g., input and output controls or review controls). It also becomes less likely that the auditor will be able to obtain audit evidence about the completeness and accuracy of such information through substantive testing alone when such information is used as audit evidence. In some circumstances, when volume and complexity of transactions are lower, management may have an information processing control that is sufficient to verify the accuracy and completeness of the data (e.g., individual sales orders processed and billed may be reconciled to the hard copy originally entered into the IT application). When the entity relies on general IT controls to maintain the integrity of certain information used by IT applications, the auditor may determine that the IT applications that maintain that information are subject to risks arising from the use of IT (CAS 315 Appendix 5.15).
| Example characteristics of an IT application that is likely not subject to risks arising from IT | Example characteristics of an IT application that is likely subject to risks arising from IT |
|---|---|
|
|
IT application is likely not subject to risks arising from IT because:
|
IT application is likely subject to risks arising from IT because:
|
OAG Guidance
CAS 315.26(b) requires us to identify IT applications and other aspects of the IT environment related to controls within the control activities component of the entity’s system of internal control that are subject to risks arising from the use of IT (e.g., IT applications the entity is relying upon to accurately process and maintain the integrity of information in the entity’s information system).
The starting point is the controls that address the risks of material misstatement that we have identified within the control activities component of the entity’s system of internal control. Refer to OAG Audit 5035.1 for further guidance related to these controls. We consider if these controls rely upon one of more IT dependencies.
Where we identify IT dependencies, we identify the IT application or other aspects of the IT environment that relate to these IT dependencies and consider if they are subject to risks arising from the use of IT. When risks arising from the use of IT are identified, we understand the IT general controls (ITGCs) that address the risks arising from the use of IT and evaluate the design and implementation of these ITGCs.
Where a manual control relies on a system‑generated report, the report is the only IT dependency type, and we conclude that we are able to substantively test the reliability of the system‑generated report for each instance of the control we plan to test, we do not consider this control to be “subject to risks arising from the use of IT” and therefore are not required to evaluate the design and implementation of ITGCs relevant to this system‑generated report. While we are not required to evaluate the design and implementation of ITGCs relevant to system‑generated reports when our testing strategy is to substantively test the reliability of each instance of the report, we consider whether it would be a more effective and efficient strategy to test the ITGC and if so, we would evaluate the design and implementation of the relevant ITGCs.
Similar to assessing the complexity of the IT environment (OAG Audit 5034) we may consider involving IT Audit when identifying IT applications and other aspects of the IT environment that may be subject to risks arising from the use of IT. IT Audit involvement could range from consulting, to coaching or completing parts of this work to support the engagement team in making these judgements.
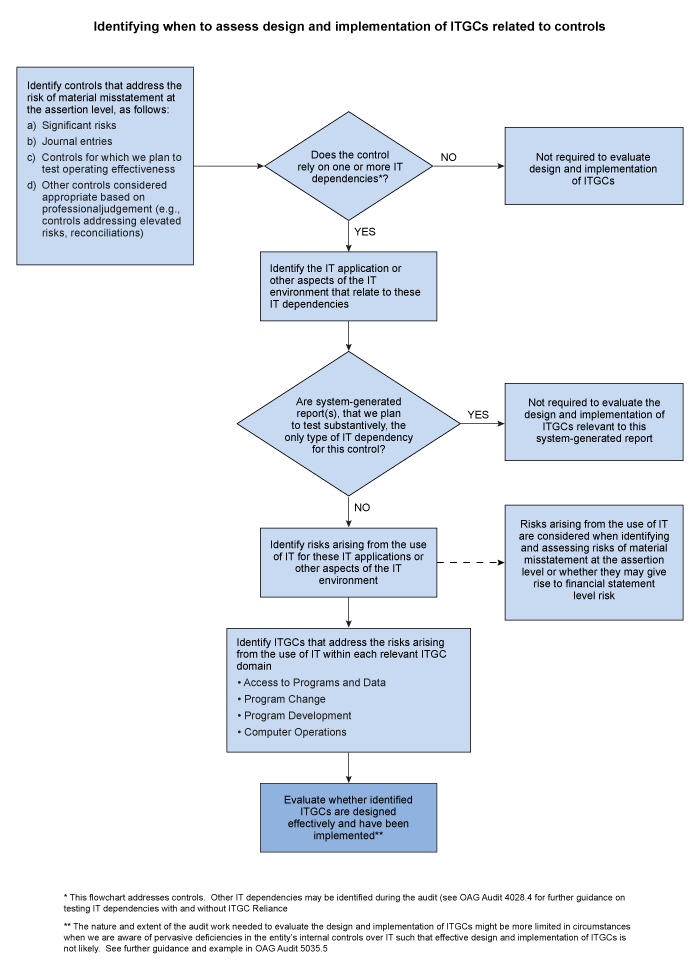
Supporting notes to the flowchart:
IT Dependencies: We identify IT dependencies when obtaining our understanding of the entity’s system of internal control, and through our end‑to‑end understanding of the data flows, processes and controls. This understanding provides a good source of information for identifying IT applications and other aspects of the IT environment related to the entity’s information processing controls.
As explained further in OAG Audit 5034, IT dependencies relate to automated or manual controls or planned substantive procedures that are dependent on IT such as system generated reports, automated calculations within applications, security that facilitates the segregation of duties or restricts direct data changes in the database and automated interfaces between IT applications.
Manual Controls: Where identified controls have no IT dependencies (i.e., the controls are entirely manual, with no reliance upon IT) we are not required to evaluate the design and implementation of ITGCs.
IT Environment: When considering IT dependencies related to controls, CAS 315 requires us to consider the entire IT environment which comprises IT applications, data and other aspects of the IT environment, including: The supporting infrastructure, specifically the network and operating systems on which applications operate The underlying databases that hold data used by applications in the information system The interfaces between IT applications
System Generated Reports: Where the only identified IT dependencies associated with a control we intend to rely upon are system generated reports for which we plan to substantively test the reliability (i.e., completeness and accuracy) of the information included in such reports, we are not required to evaluate the design and implementation of ITGCs relevant to the system‑generated reports.
For IT dependencies that do not relate to a control but are relevant to our planned substantive testing (i.e., a system‑generated report), we document IT dependencies and related aspects of the IT environment, but we do not need to identify the IT applications, or other aspects of the IT environment as being “subject to risks arising from the use of IT”. We may, nevertheless, need to evaluate the design and implementation and test the operating effectiveness of ITGCs if necessary to address the reliability of a system‑generated report (see OAG Audit 4028.4 for guidance on testing reliability of system‑generated information)
Risks arising from the use of IT: Where there are risks for which substantive procedures alone do not provide sufficient appropriate audit evidence (i.e., we will rely on ITGCs), or if there are any IT dependencies, other than system generated reports which we plan to test substantively, then risks arising from the use of IT will be identified. For the IT related risks we would identify ITGCs and evaluate their design and implementation.
CAS 315 Appendix 5.15 provides examples of characteristics to be considered when identifying whether IT applications and other aspects of IT would be subject to risks arising from IT. These characteristics include:
- Nature of the application (e.g., standalone, interfaced)
- Volume of data Complexity of the application
- Whether management is relying upon the IT application to accurately process and maintain the integrity of information in the entity’s information system
- Whether management uses system‑generated reports in their controls and whether we plan to directly test the inputs and outputs of such reports (rather to rely on controls) to cover the risk
- The information produced could be tested substantively only
In addition to IT applications that are subject to risks arising from the use of IT (e.g., IT applications the entity is relying upon to accurately process and maintain the integrity of information in the entity’s information system), we understand the other aspects of the IT environment to consider how they may impact our risk assessment. The following examples illustrate other aspects of an entity’s IT environment that could give rise to risks from the use of IT:
- We identify an automated control performed in an IT application that calculates a translation of sales invoiced in a foreign currency. The control uses a database reflecting currency exchange rates for the translation and recognition of the revenue transaction in the functional currency of the entity. In this case, we would identify both the application performing the automated currency translation calculation and the database of foreign currency translation rates as both could give rise to risks from the use of IT. This is because they are both used in this IT dependent automated control.
- During the year the entity changes from a manual process to an automated interface between application A and application B. As part of understanding this change process we identify that the client uses an IT “ticketing” tool to document and manage development of this change request and a software code management tool to enable management and review of the code changes made. We identify applications A and B relating to the interface IT dependency, and the ticketing and code management tools (i.e., applications that support change management for applications A and B). Applications A and B, the IT ticketing tool and the code management tool could give rise to risks arising from the use of IT.
- The entity uses cloud management consoles and back‑up services. These cloud based services free the entity from maintaining their own software to monitor infrastructure performance, error logging and back‑up management. The entity’s supplier portal is hosted on the cloud, and the majority of the entity’s supplier invoices, which feed into their accounts payable sub‑ledger are received through the supplier self‑service function in the portal. A system performance issue or downtime could result in invoices submitted by the suppliers not being recorded in the entity’s accounts payable sub‑ledger timely or completely and accurately, leading to a potential understatement of the entity’s recorded liabilities. The entity relies on performance reports and error logs from their cloud service provider to identify potential issues with the cloud infrastructure. These cloud services could give rise to risks arising from the use of IT.
Understand the nature and use of technology solutions
Entities are adopting technology solutions to automate processes, increase efficiencies, analyze data, increase speed of issue identification, and enhance quality. In many cases, these technology solutions have the potential to impact financial reporting. These technologies may increase the risk of material misstatement as some of these technologies are in continuous development, and may require expert skills to be developed, implemented, tested and operated. It is important for us to identify these technologies, applications or other related aspects of the IT environment, and consider the related risks arising from the use of IT. Although technology solutions may be evolving, the need to identify and understand ITGCs addressing the identified risks remains unchanged.
The following are examples of technology solutions that may be used by the entity:
- Data analysis—Technology solutions, such as Alteryx and Power Query, can be used to prepare and blend data for analysis (e.g., calculation/report used in the performance of controls or substantive procedures) by gathering, cleansing, and joining data from multiple sources. The output from data analysis technology solutions (such as an Alteryx workflow) can be an Excel spreadsheet, which may look exactly like the spreadsheet that was previously created manually.
- Visualization (reporting)—Technology solutions, such as Tableau, Power BI or Qlikview, can provide visualizations to analyze and/or present data. They are used to present raw data in a more understandable format by providing users with the ability to easily present data from various sources into one output.
- Robotic Process Automation (RPA)—RPA platforms, such as UiPath, Blue Prism or Automation Anywhere, are technology solutions that can be programmed to automate repetitive tasks. For instance, RPA may be employed to extract key metrics from customer’s financial statements or generate credit models and make preliminary decisions on credit limits. RPA may also be employed to automate the termination of user access for those identified during the periodic user access review.
- Artificial intelligence (AI)—AI represents computer systems able to perform tasks that normally require human intelligence, such as visual perception, speech recognition, decision‑making, and translation between languages. An example of AI might be the automation of reconciliations to enhance the speed of resolution of reconciling items. Through learning how individuals manually match unreconciled items, AI can be trained to execute the matching process, enabling users to limit their review to the remaining exceptions.
Blockchain—Blockchain is a type of distributed ledger technology where data is stored in blocks that are cryptographically linked together. Blocks of data are connected to the block before and after, with every additional block strengthening the verification of the previous block. Blockchains can be permissionless (open to the public) or permissioned (only available to those given access) and can be used to store a wide range of data, some examples are cryptocurrencies (e.g., Bitcoin, Ethereum), non‑fungible tokens (e.g., digital art), or supply chain (e.g., food traceability). Not all blockchains are created equally and it is important to understand the key elements of a blockchain, including but not limited to, the distributed ledger, network of participants, consensus mechanism and cryptography.
CAS Requirement
The auditor shall obtain an understanding of the control activities component, through performing risk assessment procedures, by (CAS 315.26):
(c) For such IT applications and other aspects of the IT environment identified in (b), identifying:
- The related risks arising from the use of IT; and
- The entity’s general IT controls that address such risks;
CAS Guidance
In identifying the risks arising from the use of IT, the auditor may consider the nature of the identified IT application or other aspect of the IT environment and the reasons for it being subject to risks arising from the use of IT. For some identified IT applications or other aspects of the IT environment, the auditor may identify applicable risks arising from the use of IT that relate primarily to unauthorized access or unauthorized program changes, as well as that address risks related to inappropriate data changes (e.g., the risk of inappropriate changes to the data through direct database access or the ability to directly manipulate information) (CAS 315.A173).
The extent and nature of the applicable risks arising from the use of IT vary depending on the nature and characteristics of the identified IT applications and other aspects of the IT environment. Applicable IT risks may result when the entity uses external or internal service providers for identified aspects of its IT environment (e.g., outsourcing the hosting of its IT environment to a third party or using a shared service center for central management of IT processes in a group). Applicable risks arising from the use of IT may also be identified related to cybersecurity. It is more likely that there will be more risks arising from the use of IT when the volume or complexity of automated application controls is higher and management is placing greater reliance on those controls for effective processing of transactions or the effective maintenance of the integrity of underlying information (CAS 315.A174).
Examples of risks arising from the use of IT include risks related to inappropriate reliance on IT applications that are inaccurately processing data, processing inaccurate data, or both, such (CAS 315 Appendix 5.18):
- Unauthorized access to data that may result in destruction of data or improper changes to data, including the recording of unauthorized or non‑existent transactions, or inaccurate recording of transactions. Particular risks may arise where multiple users access a common database.
- The possibility of IT personnel gaining access privileges beyond those necessary to perform their assigned duties thereby breaking down segregation of duties. Unauthorized changes to data in master files.
- Unauthorized changes to IT applications or other aspects of the IT environment.
- Failure to make necessary changes to IT applications or other aspects of the IT environment.
- Inappropriate manual intervention.
- Potential loss of data or inability to access data as required.
The auditor’s consideration of unauthorized access may include risks related to unauthorized access by internal or external parties (often referred to as cybersecurity risks). Such risks may not necessarily affect financial reporting, as an entity’s IT environment may also include IT applications and related data that address operational or compliance needs. It is important to note that cyber incidents usually first occur through the perimeter and internal network layers, which tend to be further removed from the IT application, database and operating systems that affect the preparation of the financial statements. Accordingly, if information about a security breach has been identified, the auditor ordinarily considers the extent to which such a breach had the potential to affect financial reporting. If financial reporting may be affected, the auditor may decide to understand, and test the related controls to determine the possible impact or scope of potential misstatements in the financial statements or may determine that the entity has provided adequate disclosures in relation to such security breach (CAS 315 Appendix 5.19).
In addition, laws and regulations that may have a direct or indirect effect on the entity’s financial statements may include data protection legislation. Considering an entity’s compliance with such laws or regulations, in accordance with CAS 250 (Revised), may involve understanding the entity’s IT processes and general IT controls that the entity has implemented to address the relevant laws or regulations (CAS 315 Appendix 5.20).
OAG Guidance
The nature of risks arising from the use of IT depends on the nature and characteristics of the identified IT applications or other aspects of the IT environment subject to risks arising from the use of IT (e.g., IT application the entity is relying upon to accurately process and maintain the integrity of information in the entity’s information system). For example, when revenue transactions are processed online and the entity uses an IT application to initiate and record these transactions the IT application is subject to risks such as inaccurate data processing and recognition of invalid transactions if unauthorized access to the application occurred.
Other aspects of the IT environment could lead to risks arising from the use of IT. For example, direct changes could be made to the data in the database used by an application which could circumvent application level controls. Another example would be a network and operating system that an application runs on which does not have controls to prevent unauthorized users from gaining inappropriate access or may not have appropriate intrusion detection controls to identify if there is unauthorized copying of data.
For each IT application or other aspect of the IT environment, we identify the risks arising from the use of IT. Risks arising from the use of IT are defined by CAS 315 12(i) as:
Susceptibility of information processing controls to ineffective design or operation, or risks to the integrity of information (i.e., the completeness, accuracy and validity of transactions and other information) in the entity’s information system, due to ineffective design or operation of controls in the entity’s IT processes.
When identifying risks we consider how the IT application or other aspects of IT are used to initiate, record, process, correct and incorporate in the general ledger and report transactions in the entity’s financial statements. See OAG Audit 5034 for further guidance of this understanding, and what are the risks involved in these transactions.
As part of understanding of the control activities component, we need to consider IT risks that occur at the entity level that are not associated with underlying IT dependencies and are not application specific. These are broader entity‑wide considerations of the IT environment—the “IT process‑wide considerations”, and therefore we need to consider whether these entity‑level risks may be pervasive and give rise to a risk of material misstatement at the financial statement level, see OAG Audit 5043.2 for further guidance. The two most common IT process‑wide consideration risks are:
- Duties are not appropriately segregated: When deficiencies in indirect controls (e.g., policies) affect the entity’s overall IT environment
- Governance of IT processes are not established: When deficiencies in the entity’s overall IT controls affect the entity’s overall IT environment
Some examples of risks arising from the use of IT for each aspect of the IT environment:
| Example of risks arising from the use of IT | Aspect of the IT environment | Considerations relevant to the risk |
|---|---|---|
|
|
Inappropriate individual(s) could gain the ability to amend the configuration of an application or operating system |
|
|
Authorized user accounts could be exploited by an unauthorized user |
|
|
Change(s) applied to coded application functionality could result in an error in an aspect of the IT environment, or an update to the IT environment could compromise the effective operation of automated functions that the entity relies on. These change controls apply to all aspects of the IT environment—e.g., application(s), application configuration(s), database(s), operating system(s), network(s), batch process(es) |
|
|
Direct changes to data (e.g., data fixes that bypass application controls and change the data directly in the underlying database) may result in a material misstatement |
|
|
Errors in coding or configuration when an aspect of the IT environment is being implemented or subject to major enhancement during the audit period may result in a material misstatement |
|
|
Material transactions or master‑file data may have been loaded inaccurately into the application or underlying database directly, bypassing standard application data entry controls |
|
|
(Automated) interfaces may not complete, or data fields may not match which may give rise to a material misstatement |
|
|
Loss, or inappropriate restoration of transaction records, or inability to access them as required would significantly impact financial reporting |
|
|
Inappropriate access to facilities, equipment and resources could significantly impact financial reporting, especially when the IT environment in which data is held and processed relies upon physical access controls |
See the block below Identify entity’s ITGCs that address risks arising from the use of IT for further guidance on identifying an entity’s ITGCs and their impact on the audit.
Risk considerations on the use of technology solutions
The following table provides some examples of risk considerations that may be relevant when the entity is using technology solutions:
| Technology solutions | Example of risk considerations |
|---|---|
| Data analysis and visualization technologies |
Data analysis and visualization technologies can often be more like end user computing tools. The detailed considerations related to the risks and controls in end user computing tools can be very similar to many of the risks around these types of technology solutions. When using technologies, these risks may be more similar to spreadsheets rather than production IT systems. The individuals who implement these technology solutions may be from the business—not IT—and hence not have experience with the ITGCs that need to be in place (e.g., logical access, program change). Due to the nature of technology solutions (e.g., open access, manual input of data) and the nature of the environment in which they may be developed and implemented (e.g., developed by users, hosted on LAN or local drives rather than controlled IT environment), data analysis and visualization solutions may be easier to change and may lack controls to help ensure the technology solution is consistently functioning as intended. Consider risks arising from the use of these technologies related to inappropriate changes, version control, and access to the technology. This may result in an increased inherent risk of the following errors:
Refer to OAG Audit 2051, Control implications of auditing local databases and spreadsheets for guidance on how to address these risks. |
| Robotic Process Automation (RPA) |
The development process followed when implementing RPA can be very different from legacy systems, which are normally under the control of IT environments. In a traditional development environment, a request for a change or new functionality is made, approved, and subsequently developed by someone in the IT organization. After the appropriate IT processes and controls are followed, the change is made to the application or the new application is implemented. In the traditional environment, this follows an existing change management process and would be addressed by change management controls tested by auditor’s experts. For RPA, it may also start with a request for a new automation (“bot”). However, often business users, not traditional IT developers, are responsible for developing and creating the bot. Understanding the RPA strategy, including which specific technologies are being deployed, is critical to understand the relevant risks and to be able to evaluate control design and identify potential gaps that may exist. Potential risks that we may identify are:
|
| Technology solutions Artificial Intelligence |
If entities are using these technologies in an area that impacts the audit, consider engaging auditor’s experts to assist in understanding the entity’s AI activities and assessing the risks. Some examples of potential risks include:
|
CAS Guidance
General IT controls are implemented to address risks arising from the use of IT. Accordingly, the auditor uses the understanding obtained about the identified IT applications and other aspects of the IT environment and the applicable risks arising from the use of IT in determining the general IT controls to identify. In some cases, an entity may use common IT processes across its IT environment or across certain IT applications, in which case common risks arising from the use of IT and common general IT controls may be identified (CAS 315 Appendix 5.21).
In general, a greater number of general IT controls related to IT applications and databases are likely to be identified than for other aspects of the IT environment. This is because these aspects are the most closely concerned with the information processing and storage of information in the entity’s information system. In identifying general IT controls, the auditor may consider controls over actions of both end users and of the entity’s IT personnel or IT service providers (CAS 315 Appendix 5.22).
The nature of the general IT controls typically implemented for each of the aspects of the IT environment (CAS 315 Appendix 6.1):
-
Applications
General IT controls at the IT application layer will correlate to the nature and extent of application functionality and the access paths allowed in the technology. For example, more controls will be relevant for highly‑integrated IT applications with complex security options than a legacy IT application supporting a small number of account balances with access methods only through transactions. -
Database
General IT controls at the database layer typically address risks arising from the use of IT related to unauthorized updates to financial reporting information in the database through direct database access or execution of a script or program. -
Operating system
General IT controls at the operating system layer typically address risks arising from the use of IT related to actions such as compromising other user’s credentials, adding new, unauthorized users, loading malware or executing scripts or other unauthorized programs. -
Network
General IT controls at the network layer typically address risks arising from the use of IT related to network segmentation, remote access, and authentication. Network controls may be relevant when an entity has web‑facing applications used in financial reporting. Network controls are also may be relevant when the entity has significant business partner relationships or third‑party outsourcing, which may increase data transmissions and the need for remote access.
Examples of general IT controls that may exist, organized by IT process include (CAS 315 Appendix 6.2):
a. Process to manage access:
-
Authentication
Controls that ensure a user accessing the IT application or other aspect of the IT environment is using the user’s own log‑in credentials (i.e., the user is not using another user’s credentials). -
Authorization
Controls that allow users to access the information necessary for their job responsibilities and nothing further, which facilitates appropriate segregation of duties. -
Provisioning
Controls to authorize new users and modifications to existing users’ access privileges. -
Deprovisioning
Controls to remove user access upon termination or transfer. -
Privileged access
Controls over administrative or powerful users’ access. -
User access reviews
Controls to recertify or evaluate user access for ongoing authorization over time. -
Security configuration controls
Each technology generally has key configuration settings that help restrict access to the environment. -
Physical access
Controls over physical access to the data center and hardware, as such access may be used to override other controls.
b. Process to manage program or other changes to the IT environment:
-
Change management process
Controls over the process to design, program, test and migrate changes to a production (i.e., end user) environment. -
Segregation of duties over change migration
Controls that segregate access to make and migrate changes to a production environment. -
Systems development or acquisition or implementation
Controls over initial IT application development or implementation (or in relation to other aspects of the IT environment). -
Data conversion
Controls over the conversion of data during development, implementation or upgrades to the IT environment.
c. Process to manage IT operations:
-
Job scheduling
Controls over access to schedule and initiate jobs or programs that may affect financial reporting. -
Job monitoring
Controls to monitor financial reporting jobs or programs for successful execution. -
Backup and recovery
Controls to ensure backups of financial reporting data occur as planned and that such data is available and able to be accessed for timely recovery in the event of an outage or attack. -
Intrusion detection
Controls to monitor for vulnerabilities and or intrusions in the IT environment.
OAG Guidance
Information technology general controls (ITGCs) over the entity’s IT processes support the continued proper operation of the IT environment, including the continued effective functioning of information processing controls and the integrity of information (i.e., the completeness, accuracy and validity of information) in the entity’s information system (CAS 315.12(d)). For example, access rights and restrictions intended in the design of the entity’s system of internal control.
ITGCs typically include granting and removing user access rights, administering security, enforcing authentication (e.g., password) controls, segregation of duties, and monitoring direct access and security change activities within, and across the IT environment. Deficiencies in ITGCs could compromise the effectiveness of management’s segregation of duties controls or other related control objectives by permitting inappropriate access rights. Such access could allow inappropriate changes to information maintained in the entity’s information system. Risks arising from the use of IT lead to consideration of the ITGCs that address such risks. Well designed, implemented and maintained ITGCs create the foundation upon which other controls can operate to address these risks.
Example:
The following risk has been identified in relation to an entity’s accounts receivable balances “Method (including any model), significant assumptions and data used to estimate the allowance for doubtful accounts are not appropriate/reasonable” and the following control responding to the risk has been identified:
Detective, IT Dependent manual control: The system generated A/R aging report (which is configured to allocate invoices into aging categories) is reviewed by the finance manager for significantly aged customer balances and known issues in the accounts receivable sub‑ledger and the corresponding allowance for doubtful accounts to ensure account balances are adequately reserved. Differences are investigated and resolved on a timely basis. We apply the illustrative flowchart in the block above Identify IT applications and other aspects of the IT environment to identify IT dependencies, related aspects of the IT environment subject to risks arising from the use of IT, and the related ITGCs that address these risks:
| IT Dependency | IT environment aspect | Risks arising from the use of IT | ITGCs that address the risk |
|---|---|---|---|
|
Report: System generated trade receivable aging report Automated Calculation: automated allocation of invoices into aging categories |
Application ABC used to manage revenue, accounts receivable and create the trade receivable aging report |
Unauthorized or untested changes, or the failure to make necessary changes to application configurations prevent the IT environment from processing transaction records completely and accurately High‑risk/powerful accounts (i.e., developers’ access to production environment) can bypass program changes controls. |
IT process‑wide considerations—Policies are maintained for segregation of duties within IT Program change: Changes to the IT environment are adequately tested and approved before being migrated into production Access to program and data: No individuals with developer’s access have access to the production environment (or if no system enforced segregation is in place, adequate monitoring controls over changes released by developers exist). Access to programs and data—Super‑user/ administrative application transactions or activities and sensitive generic IDs are monitored |
This example demonstrates a risk may be addressed by an entity’s ITGCs but is not intended to address all potential risks arising from the use of IT.
There may be other considerations and controls to be tested to enable reliance on this report, depending on the determined testing approach. For example, information processing controls over the preparation and maintenance of the report (see OAG Audit 4028.4 for guidance on testing reliability of information generated by an IT application).
As noted in OAG Audit 5031, entity level controls (ELCs) operate at the entity level. IT process‑wide considerations are IT controls that have impact across more than one business process and are considered when evaluating the effectiveness of information processing or direct entity‑level controls at the transaction level within a business process. We also consider if these IT process‑wide considerations could relate to pervasive risks, see the block above Identify risks arising from the use of IT.
ITGCs help determine the continued reliability of information generated by applications. ITGCs are typically categorized in four domains, as described below.
| Domain* | Description |
|---|---|
| Access to programs and data (security) | The domain objective is to ensure that only authorized access is granted to the IT applications and other aspects of the IT environment upon authentication of a user’s identity. Controls over access to the IT environment include the processes used by the entity to add, delete, and change users (both business users and IT personnel) and their related access rights according to the control objectives established in the design of the control (that is, to achieve the entity’s objectives for appropriately restricted access and segregation of duties). |
| Program change | The domain objective is to ensure that changes to the IT application and other aspects of the IT environment are requested, authorized, performed, tested, and implemented to achieve management’s IT control objectives. |
| Program development |
The domain objective is to ensure that IT applications and other aspects of the IT environment are developed, configured, and implemented to achieve management’s control objectives. This includes development or acquisition or implementation controls and data conversion controls. |
| Computer operations | The domain objective is to ensure that information in the IT applications and other aspects of the IT environment is processed completely and accurately in accordance with management’s control objectives, and that processing problems are identified and resolved completely and accurately to maintain the integrity of financial data. |
*The ITGC domains cover the IT environment as a whole and relate to the IT processes in CAS 315, as per the mapping in the block above Overview.
For risks arising from an entity’s use of IT we consider which of the four ITGC domains may be relevant. For example, for an entity that relies on a number of applications, the Program development domain may only be relevant when significant development, implementation, or conversion projects impact the risk of material misstatement. Refer to the block below ITGC Domains for guidance on each ITGC domain.
The following table provides some examples of ITGCs commonly implemented to address risks arising from the use of IT, categorized by IT domain.
|
Access to programs and data |
|
|
Program change |
These change controls apply to all aspects of the IT environment – e.g., application(s), application configuration(s), database(s), operating system(s), network(s), batch process(es)
|
|
Program development |
|
|
Computer operations |
|
| Example of risks arising from the use of IT | IT Domain | Examples of ITGCs implemented to address risks arising from the use of IT |
|---|
Please see the block below Cybersecurity risk assessment considerations for further consideration of the risks and controls relating to cybersecurity that could affect one or more of the ITGC domains.
CAS Guidance
Examples of general IT controls that may exist, organized by IT process include (CAS 315 Appendix 6.2(a)):
Process to manage access:
◦ Authentication
Controls that ensure a user accessing the IT application or other aspect of the IT environment is using the user’s own log‑in credentials (i.e., the user is not using another user’s credentials).
◦ Authorization
Controls that allow users to access the information necessary for their job responsibilities and nothing further, which facilitates appropriate segregation of duties.
◦ Provisioning
Controls to authorize new users and modifications to existing users’ access privileges.
◦ Deprovisioning
Controls to remove user access upon termination or transfer.
◦ Privileged access
Controls over administrative or powerful users’ access.
◦ User access reviews
Controls to recertify or evaluate user access for ongoing authorization over time.
◦ Security configuration controls
Each technology generally has key configuration settings that help restrict access to the environment.
◦ Physical access
Controls over physical access to the data center and hardware, as such access may be used to override other controls.
The table below illustrates examples of general IT controls to address examples of risks arising from the use of IT, including for different IT applications based on their nature.
| Risks | Controls | IT Applications | ||
|---|---|---|---|---|
| Example Risks Arising from the Use of IT | Example General IT Controls | Non‑complex commercial software—Applicable (yes / no) |
Mid‑size and moderately complex commercial software or IT applications—Applicable (yes / no) | Large or complex IT applications (e.g., ERP systems)—Applicable (yes / no) |
| User‑access privileges: Users have access privileges beyond those necessary to perform their assigned duties, which may create improper segregation of duties | Management approves the nature and extent of user‑access privileges for new and modified user access, including standard application profiles/roles, critical financial reporting transactions, and segregation of duties | Yes—instead of user access reviews noted below | Yes | Yes |
| Access for terminated or transferred users is removed or modified in a timely manner | Yes—instead of user access reviews below | Yes | Yes | |
| User access is periodically reviewed | Yes—instead of provisioning/ Deprovisioning controls above | Yes‒for certain applications | Yes | |
| Segregation of duties is monitored and conflicting access is either removed or mapped to mitigating controls, which are documented and tested | N/A—no system enabled segregation | Yes‒for certain applications | Yes | |
| Privileged‑level access (e.g., configuration, data and security administrators) is authorized and appropriately restricted | Yes—likely at IT application layer only | Yes‒at IT application and certain layers of IT environment for platform | Yes—at all layers of IT environment for platform | |
| Direct data access: Inappropriate changes are made directly to financial data through means other than application transactions. | Access to application data files or database objects/tables/data is limited to authorized personnel, based on their job responsibilities and assigned role, and such access is approved by management | N/A | Yes‒for certain applications and databases | Yes |
| System settings: Systems are not adequately configured or updated to restrict system access to properly authorized and appropriate users. |
Access is authenticated through unique user IDs and passwords or other methods as a mechanism for validating that users are authorized to gain access to the system. Password parameters meet company or industry standards (e.g., password minimum length and complexity, expiration, account lockout) |
Yes—password authentication only | Yes–mix of password and multi‑factor authentication | Yes |
| The key attributes of the security configuration are appropriately implemented | N/A—no technical security configurations | Yes‒for certain applications and exist databases | Yes | |
OAG Guidance
Access to Programs and Data*—Domain objective:
To ensure that only authorized access is granted to the IT applications and other aspects of the IT environment upon authentication of a user’s identity. Controls over access to the IT environment include the processes used by the entity to add, delete, and change users (both business users and IT personnel) and their related access rights according to the control objectives established in the design of the control (that is, to achieve the entity’s objectives for appropriately restricted access and segregation of duties).
*Access to Programs and Data covers access to the IT environment as a whole and relates to the “Manage Access” domain in CAS 315, as per the mapping in the block above Overview.
When understanding controls over access to the IT environment, we typically understand the entity’s IT security risks, its approach to IT security, and the relevant aspects of its specific IT security architecture (e.g., “single sign‑on” to the network versus application‑level security), before deciding which layer(s) of security and access controls are important to address the identified risks arising from the use of IT (i.e., IT risks relevant to the preparation of the financial statements).
The sub‑components of Access to Programs and Data domain typically include:
- Management of security activities
- Security administration
- Direct access to data (databases or data files)
- Operating system security
- Utilities (e.g., job schedulers, reporting tools)
- Network security
- Physical security
Examples of ITGCs that may exist to manage access to the IT environment typically include the following (CAS 315 Appendix 6.2(a)):
- Authentication
- Authorization
- Provisioning
- Deprovisioning
- Privileged access
- User access reviews
When understanding the above, not all sub‑components and ITGCs may be applicable to every entity, and other risk factors may exist that may need to be considered. The manner in which access is requested, authorized and controlled varies among entities, depending on the size and complexity of the environment and volume and types of access processed.
Consider using applicable territory technical platform practice aids and work programs to assist in our evaluation of controls over access in the Access to Programs and Data domain.
We obtain this understanding of the sub‑components and ITGCs to help determine which layer(s) of security controls are relevant to the preparation of the financial statements and obtain evidence about whether the more important elements exist and are implemented. For instance, perimeter or network security and anti‑hacking controls, such as firewalls and intrusion detection systems, may be relevant to the preparation of the financial statements if there are material financial reporting risks that are not adequately addressed by application‑level security alone. Additionally, if utility applications such as job schedulers or reporting tools are used to support key reports or interfaces, these utilities may be relevant to the preparation of the financial statements. The following graphic illustrates the different layers of security in the IT environment:
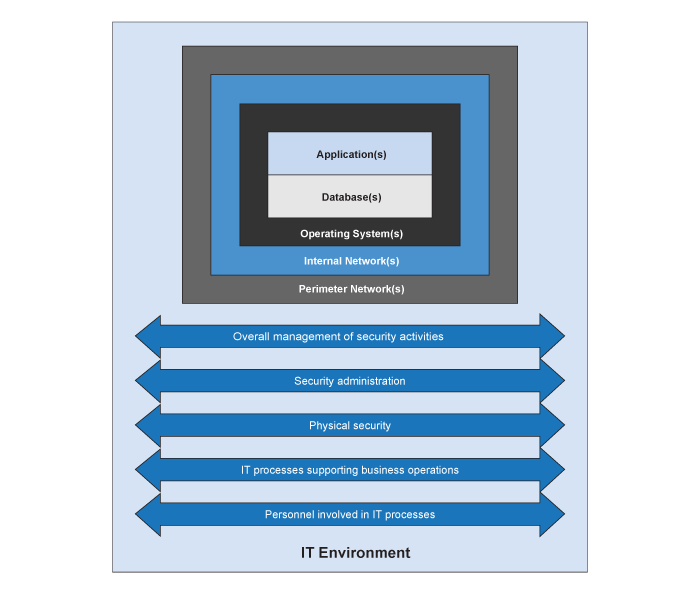
Direct access to databases or data files
Access to data is a routine and essential aspect of operating most computerized accounting systems. However, management needs to implement an appropriate balance of controls to mitigate the risk of a material misstatement from unauthorized or erroneous changes to accounting data via direct data access. We generally focus our direct data access risk assessment at the database or application layers. There is generally a lower risk of direct data access at the operating system level, as data is not expected to be held, nor directly accessed at the operating system level. As illustrated in the figure above, these are all within the internal network. The perimeter network and security are where the cross‑over into the external, web‑facing IT environment (e.g., the internet) occurs. As noted above, the perimeter network is where intrusion prevention/detection and monitoring controls are set up to prevent attacks (e.g., ransomware) which may prevent the entity from accessing its critical infrastructure or data. Other cybersecurity risks and controls may relate to access to programs and data, and/or other ITGC domains. See the block below Cybersecurity risk assessment considerations for additional guidance on cybersecurity risks and controls.
When access to data is restricted to authorized users in the IT department, operational risks such as accidental system shutdown or the incorrect restore of data/ interfaces or programs tend to be greater than the risks of intentional misstatement or other types of fraud. If personnel responsible for financial reporting (e.g., finance controller) have direct access to change data, we may need to consider if this may be an indicator of potential fraud risks. Consider likelihood, not just magnitude when evaluating the risks associated with privileged access.
The following considerations may be helpful for identifying ITGCs in the Access to Programs and Data domain that address the risks arising from an entity’s use of IT. See the block above Identify risks arising from the use of IT for further guidance on identifying risks arising from the use of IT. Note: Not all points of focus are relevant to every entity, and other risk factors may exist that will need to be considered.The table below provides examples of risks and considerations for the audit split by sub‑component and referencing these ITGCs.
| Risk* | Considerations for the audit |
|---|---|
| Application end-users bypass system-enforced authorization and segregation of duties controls. |
Security administration
|
| High‑risk/powerful accounts (e.g., super‑users) bypass systems‑enforced authorization and segregation of duties controls. |
Management of security activities
Network security
|
| Unauthorized access to facilities, equipment and resources is not prevented |
Physical security Controls might be necessary in certain environments to ensure that an organization’s systems are protected from unauthorized physical access. If relevant, consider:
|
| Improper direct changes are made to underlying transaction records and/or master data |
Data security
|
| Weak password controls or security configurations allow access rights to be circumvented | Operating system security
|
*Please see the block below Cybersecurity risk assessment considerations for further consideration of the risks and controls relating to cybersecurity that could affect one or more of the ITGC domains.
CAS Guidance
Examples of general IT controls that may exist, organized by IT process include (CAS 315 Appendix 6.2(b)):
Process to manage program or other changes to the IT environment:
- Change management process
Controls over the process to design, program, test and migrate changes to a production (i.e., end user) environment.
- Segregation of duties over change migration
Controls that segregate access to make and migrate changes to a production environment.
The table below illustrates examples of general IT controls to address examples of risks arising from the use of IT, including for different IT applications based on their nature.
| Risks | Controls | IT Applications | ||
|---|---|---|---|---|
| Example Risks Arising from the Use of IT | Example General IT Controls | Non‑complex commercial software—Applicable (yes / no) |
Mid‑size and moderately complex commercial software or IT applications—Applicable (yes / no) | Large or complex IT applications (e.g., ERP systems)—Applicable (yes / no) |
|
Application changes: Inappropriate changes are made to application systems or programs that contain relevant automated controls (i.e., configurable settings, automated algorithms, automated calculations, and automated data extraction) or report logic. |
Application changes are appropriately tested and approved before being moved into the production environment |
N/A ‒ would verify no source code installed |
Yes‒for non‑commercial software |
Yes |
| Access to implement changes into the application production environment is appropriately restricted and segregated from the development environment | NA | Yes‒for non‑commercial software | Yes | |
| Database changes: Inappropriate changes are made to the database structure and relationships between the data. | Database changes are appropriately tested and approved before being moved into the production environment | N/A–no database changes made at entity | Yes–for non‑commercial software | Yes |
| System software changes: Inappropriate changes are made to system software (e.g., operating system, network, change‑management software, access‑control software). | System software changes are appropriately tested and approved before being moved to production | N/A–no system software changes are made at entity | Yes | Yes |
OAG Guidance
|
Program Change*—Domain objective: To ensure that changes to the IT application and other aspects of the IT environment are requested, authorized, performed, tested, and implemented to achieve management’s control objectives. *Program Change covers changes to the IT environment as a whole and relates to the “Manage Change” domain in CAS 315, as per the mapping in the block Overview. Note: development and data conversion are covered in the Program Development domain below. |
The entity is to demonstrate, with reasonable assurance, that sufficient change controls are applied consistently to all aspects of the IT environment—including IT applications, network, databases or operating system(s) that are subject to risks arising from the use of IT. The sub‑components of the Program Change domain typically include:
- Management of maintenance activities
- Specification, authorization and tracking of change requests
- Construction
- Testing and quality assurance
- Program implementation
- Documentation and training
- Data changes
- Segregation of duties
Examples of ITGCs that may exist to manage changes to the IT environment typically include the following (CAS 315 Appendix 6.2(b)):
- Change management process
- Segregation of duties over change migration
When understanding the above, not all sub‑components and ITGCs may be applicable to every entity, and other risk factors may exist that may need to be considered. The manner in which changes are identified, tracked, and controlled varies among entities, depending on the size and complexity of the environment and volume and types of changes processed. When determining our approach to addressing the risk associated with program changes, we obtain an understanding of the nature of changes made during the period under audit (e.g., changes to source code, configuration of database or operating systems, data changes, etc.).
When considering the risks arising from the use of IT associated with IT changes, we first obtain an understanding of the nature of changes made during the period under audit (i.e., changes to source code, configuration of database or operating systems, etc.) for identified applications and other aspects of the IT environment. Where changes impact on identified IT dependencies, we may choose to rely on change controls to address the risks arising from the use of IT. An important aspect of effective change controls is the ability of the entity to understand if, and when, a key automated information processing control or IT‑dependent manual control has changed, whether they have been considered for testing in the change process, and whether change controls are applied consistently. This will usually entail some degree of linkage between the change activities in IT and overall ownership and monitoring. This is also a necessary criteria, not only to support a benchmarking strategy (as described in OAG Audit 6054), but also to use our testing of ITGCs as the basis for relying on the ongoing operating effectiveness of information processing controls and IT dependent manual controls in the current audit period. We can possibly eliminate or significantly limit our testing of change controls when the risk of significant changes to a key application is low. For example, during the risk identification process where client’s use off‑the‑shelf software with no customization, or when other reliable evidence demonstrates that a relevant automated or IT‑dependent manual control hasn’t been changed since it was last tested (e.g., a system report or evidence showing last date modified).
Determining the full population of changes
Monitoring and testing that all relevant changes have been subjected to the entity’s change controls can be made easier when the entity’s IT environment can produce reliable evidence (i.e., an “audit trail”) of the full population of changes. For example, if a reliable report of all compilation dates of all changes placed in production is available, management can more readily demonstrate that every change went through its controlled process.
However, not all IT environments are designed to produce reliable, automated information about the population of changes. Some will log only the date of last modification. Others may be able to log all changes, but perhaps those logs can be circumvented or overwritten by those with direct access to the production environment. A lack of IT generated change data does not in itself preclude management from being able to demonstrate, with reasonable assurance, that the entity’s change controls are applied consistently to relevant changes. Some factors to consider in evaluating whether there can be reasonable assurance that all such changes have been dealt with appropriately typically include:
- The types of applications used, whether the entity has access to the source code, and the nature and volume of routine changes
- Whether changes are rigorously tracked, electronically or manually, by parties who are independent from those requesting or making the changes, using data that cannot be altered by those requesting or making the changes
- Whether separate environments are maintained for development, testing and production, and only the appropriate individuals have access to each of those environments
- Whether responsibilities are segregated appropriately such that the person responsible for identifying, tracking, and reporting on the status of change requests does not have accounting or finance responsibilities
- Whether there is an automated “audit trail” record enabled for the IT environment
The guidance below can be considered when assessing the risks arising from the use of IT, see the block Identify risks arising from the use of IT for further guidance on identifying risks arising from the use of IT. The following considerations may be helpful for identifying ITGCs in this domain that address the risks arising from the use of IT identified at the entity. Note: Not all points of focus are relevant to every entity, and other risk factors may exist that will need to be considered. For example, cybersecurity risks and controls may relate to program change, and/or other ITGC domains. Please see the block Cybersecurity risk assessment considerations for additional guidance on cybersecurity risks and controls.
The table below provides examples of risks and considerations for the audit split by sub‑component and referencing these ITGCs.
| Risk* | Considerations for the audit |
|---|---|
| Unauthorized or untested changes, or the failure to make necessary changes to application configurations/ batch processes/ operating system/ network prevent systems from processing transaction records completely and accurately |
Management of maintenance activities
Specification, authorization and tracking of change requests
Construction controls ensure that changes are designed and performed to support the achievement of management’s information processing control objectives. Consider the following:
Testing and quality assurance
Implementation
Documentation and training
Segregation of duties
|
*Please see the block Cybersecurity risk assessment considerations for further consideration of the risks and controls relating to cybersecurity incidents that could affect one or more of the ITGC domains.
CAS Guidance
Examples of general IT controls that may exist, organized by IT process include (CAS 315 Appendix 6.2(b)):
Process to manage program or other changes to the IT environment:
- Change management process
Controls over the process to design, program, test and migrate changes to a production (i.e., end user) environment.
- Segregation of duties over change migration
Controls that segregate access to make and migrate changes to a production environment.
- Systems development or acquisition or implementation
Controls over initial IT application development or implementation (or in relation to other aspects of the IT environment).
- Data conversion
Controls over the conversion of data during development, implementation or upgrades to the IT environment.
The table below illustrates examples of general IT controls to address examples of risks arising from the use of IT, including for different IT applications based on their nature.
| Risks | Controls | IT Applications | ||
|---|---|---|---|---|
| Example Risks Arising from the Use of IT | Example General IT Controls | Non‑complex commercial software –Applicable (yes / no) | Mid-size and moderately complex commercial software or IT applications – Applicable (yes / no) | Large or complex IT applications (e.g., ERP systems) –Applicable (yes / no) |
| Application changes: Inappropriate changes are made to application systems or programs that contain relevant automated controls (i.e., configurable settings, automated algorithms, automated calculations, and automated data extraction) or report logic. | Application changes are appropriately tested and approved before being moved into the production environment | N/A—would verify no source code installed | Yes—for non‑commercial software | Yes |
| Access to implement changes into the application production environment is appropriately restricted and segregated from the development environment | N/A | Yes for non‑commercial software | Yes | |
| Database changes: Inappropriate changes are made to the database structure and relationships between the data. | Database changes are appropriately tested and approved before being moved into the production environment | N/A—no database changes made at entity | Yes—for non‑commercial software | Yes |
| System software changes: Inappropriate changes are made to system software (e.g., operating system, network, change‑management software, access‑control software). | System software changes are appropriately tested and approved before being moved to production | N/A – no system software changes are made at entity | Yes | Yes |
| Data conversion: Data converted from legacy systems or previous versions introduces data errors if the conversion transfers incomplete, redundant, obsolete, or inaccurate data. | Management approves the results of the conversion of data (e.g., balancing and reconciliation activities) from the old application system or data structure to the new application system or data structure and monitors that the conversion is performed in accordance with established conversion policies and procedures | N/A – Addressed through manual controls | Yes | Yes |
OAG Guidance
Program Development*—Domain objective:
To ensure that IT applications and other aspects of the IT environment are developed, configured, and implemented to achieve management’s control objectives. This includes development or acquisition or implementation controls and data conversion controls.
*Program Development covers development of the IT environment as a whole and relates to the “Manage Change” domain in CAS 315, as per the mapping in the block Overview.
This domain is relevant only where significant development, implementation, or conversion projects exist or are anticipated that will impact the risk of material misstatement to the current year’s financial statements. ITGCs related to the Program Development domain will be identified to address risks arising from the use of IT related to new IT applications or other aspects of IT developed, configured and implemented in the period. For example, when there is a new IT application used in an identified control, we may have identified a risk related to incompletely or inaccurately processed data in this application. Therefore, in order to address the risk, management implemented ITGCs to test and approve the IT application.
CAS 315 includes development in the “Manage Change” IT process. As above, the Program Development domain is only relevant where the entity has significant development, implementation or conversion projects in the period. Development may not occur every year. Separating Program Development from Program Change assists us in a more granular evaluation of how change occurs in the entity’s IT environment. It also helps us to identify and assess the risks arising from the use of IT at the domain level:
- Where the entity undertakes no development in the period, no Program Development domain risks arise from the use of IT
- Where the entity undertakes development in the period, the Program Development domain is where development risks arising from the use of IT are documented
ITGCs related to development will vary from entity to entity and project to project, depending on the risks identified. The most important development controls tend to operate close to the implementation date. We also monitor and assess new risks that may arise from development activities (i.e., temporary super user access among key financial personnel), as well as controls that the entity might put in place temporarily during the conversion period.
For example, the entity plans to implement a new financial application this year. This new system will impact the entity’s financial statements for that audit year. It is often more effective and efficient to understand newly implemented or changed information processing controls and data conversions by reviewing the entity’s controls in the development cycles than it is to test the controls solely in the live, post‑implementation environment.
Professional judgment is needed to determine whether we understand development controls in the current year, particularly for implementation that will not directly impact financial reporting risk until a subsequent year. Refer to the table below for considerations when assessing the risks arising from the use of IT within the Program Development domain. ITGCs related to development are important to many audits, but their overall relevance is more client specific.
We review significant developments and assess the financial impact associated with the entity’s development where the development relates to a control identified within the control Activities component. For example, if an entity implements a new IT application during the period under audit that includes controls and IT dependencies relating to a risk of material misstatement, we obtain an understanding of the implementation process and identify the risks arising from the use of IT to determine whether the development controls address these risks. This understanding is helpful when considering if it is efficient and effective to test controls to obtain evidence over the new system, implementation process and conversion of data. In circumstances where the development relates to a risk arising from the use of IT, we obtain the supporting documentation.
The sub‑components of the Program Development domain typically include:
- Management of development and implementation activities
- Project initiation, analysis, and design
- Construction/package selection
- Testing and quality assurance
- Data conversion
- Program implementation
- Documentation and training
- Segregation of duties
Example of ITGCs that may exist to manage development of the IT environment typically include the following (CAS 315 Appendix 6.2(b)):
- Change management process
- Segregation of duties over change migration
- Systems development or acquisition or implementation
- Data conversion
We determine the activities that are relevant and the controls based on the entity’s unique IT environment. The following considerations may be helpful for identifying ITGCs in this domain that address the identified risks arising from the use of IT at the entity. See the block Identify risks arising from the use of IT for further guidance on identify risks arising from the use of IT. Note: Not all considerations are relevant to every entity, and other risk factors may exist that will need to be considered. For example, cybersecurity risks and controls may relate to program development, and/or other ITGC domains. Please see the block Cybersecurity risk assessment considerations for additional guidance on cybersecurity risks and controls.
When understanding the above, not all sub‑components and ITGCs may be applicable to every entity, and other risk factors may exist that may need to be considered. The table below provides examples of risks and considerations for the audit split by sub‑component and referencing these ITGCs.
| Risk* | Considerations for the audit |
|---|---|
| Newly implemented (or significantly enhanced) systems incompletely or inaccurately process data (e.g., due to erroneous coding/configuration) |
Overall management of development activities
Project initiation, analysis and design
Construction/package selection
Testing and quality assurance
Program implementation
Documentation and training
Segregation of duties
|
| Transaction records and/or master data are not completely and accurately migrated | Data conversion
|
*Please see in the block Cybersecurity risk assessment considerations for further consideration of the risks and controls relating to cybersecurity incidents that could impact across one or more of the ITGC domains.
Auditing Enterprise Resource Planning Systems Implementation and Upgrades
Implementation and significant upgrades/changes to our client’s Enterprise Resource Planning (ERP) systems often result in business process changes. The results of such changes may mean transactions are not processed the way they used to be, reports may be redesigned and changes in controls are implemented. For example, some upgrades/changes result in moving the ERP to be hosted in a cloud environment which means that the supporting infrastructure may change. Sometimes when an entity upgrades/changes its ERP there is a movement away from traditional preventative controls, and a movement of some controls to those that have both preventive and detective characteristics:
- Real time controls designed to avoid creating a ‘hard stop’ that interrupts business operations, while enabling controls that support the business, or
- Hybrid controls that have both preventive and detective characteristics.
When understanding and evaluating the design of those controls we consider both preventive and detective characteristics of the control to the extent they are responsive to the identified risk of material misstatement.
See OAG Audit 5034 for guidance and examples of different types of Controls.
The audit of the financial statements needs to consider the impact of these ERP implementations and/or upgrades as part of risks arising from the use of IT. There is a presumption that any client with systems of sufficient complexity and scope to warrant the expenditures to implement an ERP system would have an impact on our audit strategy. It is also necessary to recognize that a large‑scale ERP implementation may create an environment in which it is unlikely that an effective audit can be conducted without adopting, to a significant degree, a controls‑oriented approach.
Each ERP implementation is unique (e.g., no two SAP implementations are the same), thus consider the impact of the implementation on internal control and make a determination about how to audit effectively in the individual client circumstances. The points that need to be considered during such changes are:
- IT Audit involvement to understand the impact of the ERP to the control environment. Additionally, it is normally expected that Information technology general controls (ITGCs) are tested.
- How the ERP implementation will impact the inherent risk factors and the overall risk assessment process necessary to understand and audit the implementation. During the initial year of an ERP implementation or significant upgrade, early planning is conducted to:
- Identify which controls that address the risks of material misstatement at the assertion level are impacted by new or changed ERP modules
- Identify the other aspects of the IT environment that could be subject to risks arising from the use of IT, e.g.
- Interfaces (ERPs are often linked to other systems that in turn need controls to ensure that all inputs are received for processing and all outputs are distributed appropriately)
- Network, database and application level security, and
- Other risks and related ITGCs (i.e., in this instance the Program development ITGC domain is likely to be important)
- Obtain the entity’s implementation timetable to determine when and where the ERP implementation will impact the audit
- Impact to controls—has a baseline understanding and assessment of internal control been established by:
- Internal audit reviews (pre‑implementation or post‑implementation controls assessment)?
- OAG’s evaluation of the design and implementation of controls undertaken as part of the audit?
- Assessments by other reputable firms?
- Documentation of business processes and controls for the new ERP processing environment?
- What are the entity’s and the Audit Committee’s expectations of the audit?
- Does the entity expect the OAG team to understand how to access information using its ERP system?
- Do they expect the OAG team to place reliance on the new processing and internal control environment?
- What is the impact on the OAG team’s prior audit knowledge?
- Has the ERP system changed the process or methods for performing significant or a majority of the business processes? Have the entity’s business processes moved from manual to automated processes?
- Has the ERP implementation changed the entity’s internal control from manual detective‑based controls to automated preventive‑based controls or some combination of both?
- Has the ERP system completely changed the ITGCs? Has the ERP system replaced all the legacy systems that the PwC team’s knowledge and internal control understanding was based on?
- Is the mapping of the entity’s significant business processes and systems still accurate?
Related Guidance
See OAG Audit 3102 for guidance on the use of IT Audit.
CAS Guidance
Examples of general IT controls that may exist, organized by IT process include (CAS 315 Appendix 6.2(c)):
Process to manage IT operations
- Job scheduling
Controls over access to schedule and initiate jobs or programs that may affect financial reporting.
- Job monitoring
Controls to monitor financial reporting jobs or programs for successful execution.
- Backup and recovery
Controls to ensure backups of financial reporting data occur as planned and that such data is available and able to be accessed for timely recovery in the event of an outage or attack.
- Intrusion detection
Controls to monitor for vulnerabilities and or intrusions in the IT environment.
The table below illustrates examples of general IT controls to address examples of risks arising from the use of IT, including for different IT applications based on their nature.
| Risks | Controls | IT Applications | ||
|---|---|---|---|---|
| Example Risks Arising from the Use of IT | Example General IT Controls | Non‑complex commercial software— Applicable (yes/no) |
Mid‑size and moderately complex commercial software or IT applications— Applicable (yes / no) | Large or complex IT applications (e.g., ERP systems— Applicable (yes/no) |
| Network: The network does not adequately prevent unauthorized users from gaining inappropriate access to information systems. | Access is authenticated through unique user IDs and passwords or other methods as a mechanism for validating that users are authorized to gain access to the system. Password parameters meet company or professional policies and standards (e.g., password minimum length and complexity, expiration, account lockout) | N/A—no separate network authentification method exists | Yes | Yes |
| Network is architected to segment web‑facing applications from the internal network, where ICFR relevant applications are accessed | N/A—no network segmentation employed | Yes—with judgement | Yes—with judgement | |
| On a periodic basis, vulnerability scans of the network perimeter are performed by the network management team, which also investigates potential vulnerabilities | N/A | Yes—with judgement | Yes—with judgement | |
| On a periodic basis, alerts are generated to provide notification of threats identified by the intrusion detection systems. These threats are investigated by the network management team | N/A | Yes—with judgement | Yes—with judgement | |
| Controls are implemented to restrict Virtual Private Network (VPN) access to authorized and appropriate users | N/A—no VPN | Yes—with judgement | Yes—with judgement | |
| Data backup and recovery: Financial data cannot be recovered or accessed in a timely manner when there is a loss of data. | Financial data is backed up on a regular basis according to an established schedule and frequency | N/A—relying on manual backups by finance team | Yes | Yes |
| Job scheduling: Production systems, programs, or jobs result in inaccurate, incomplete, or unauthorized processing of data. | Only authorized users have access to update the batch jobs (including interface jobs) in the job scheduling software | N/A—no batch jobs | Yes—for certain applications | Yes |
| Critical systems, programs, or jobs are monitored, and processing errors are corrected to ensure successful completion. | N/A—no job monitoring | Yes—for certain applications | ||
OAG Guidance
Computer Operations—Domain objective:
To ensure that the IT applications and other aspects of the IT environment are processed completely and accurately in accordance with management’s control objectives, and that processing problems are identified and resolved completely and accurately to maintain the integrity of financial data.
*Computer Operations covers IT operations across the IT environment as a whole and relates to the “Manage IT Operations” domain in CAS 315, as per the mapping in the block Overview.
Activities in IT operations often present operational risk, not a risk of material misstatement, depending on the entity’s specific circumstances. Some elements of IT operations may be relevant to the preparation of the financial statements, particularly when they serve not only as ITGCs, but also as information processing controls that directly support relevant financial statement assertions. For example, job scheduling is an IT activity that could directly impact the completeness and accuracy of financial data if it were to break down. Similarly, backup and recovery procedures may be important to the risk of financial misstatement if data recoveries are frequent, such as when systems are unstable, or if there is a cyber incident that restricts access to the live environment. ITGCs related to IT operations are important to many audits, but their overall relevance is more entity level specific. We may identify activities in IT operations that serve as information processing controls as part of the control activities component. The sub‑components of the Computer Operations domain typically include:
- Management of computer operations activities
- Batch scheduling and processing
- Real‑time processing
- Backup and problem management
- Disaster recovery
Example of ITGCs that may exist to manage computer operations typically include the following (CAS 315 Appendix 6.2(c)):
- Job scheduling
- Job monitoring
- Backup and recovery
- Intrusion detection
The following considerations may be helpful for identifying ITGCs in this domain that address the risks arising from the use of IT identified at the entity. See the block Identify risks arising from the use of IT for further guidance on identifying risks arising from the use of IT. Note: Not all considerations are relevant to every entity, and other risk factors may exist that will need to be considered. For example, cybersecurity risks and controls may relate to computer operations, and/or other ITGC domains. Please see the block cybersecurity risk assessment considerations for additional guidance on cybersecurity risks and controls.
When understanding the above, not all sub‑components and ITGCs may be applicable to every entity, and other risk factors may exist that may need to be considered. The manner in which computer operations are set up, authorized and controlled varies among entities, depending on the size and complexity of the environment and volume and types of operations undertaken. The tables below provide examples of risks and considerations for the audit split by sub‑component and referencing these ITGCs.
| Risk* | Considerations for the audit |
|---|---|
| Inappropriate changes to, manual intervention in, or failures in batch processes. |
Overall management of IT operations activities
Batch scheduling and processing
|
| Transaction records are lost (e.g., due to system failure) and data is not recoverable or is corrupted/ duplicated in the recovery process. |
Backup and problem management
|
| Transaction records transferred between systems are incomplete or inaccurate. |
Real‑time processing
|
| Cyber and ransomware attacks exploit vulnerabilities resulting in manipulation and/ or destruction of data that impact the financial statements or affect system availability impacting timely financial reporting. |
|
| Unpatched IT applications, or other aspects of the IT environment, lead to exploiting known security vulnerabilities resulting in the manipulation and/ or destruction of data that impacts the financial statements or affects availability of the IT environment impacting timely financial reporting |
|
| Ransomware attacks result in inaccessible systems impacting system availability and the entity’s ability to prepare financial reporting on a timely basis |
|
*Please see the block Cybersecurity risk assessment considerations for further consideration of the risks and controls relating to cybersecurity that could affect one or more of the ITGC domains.
CAS Guidance
The auditor’s consideration of unauthorized access may include risks related to unauthorized access by internal or external parties (often referred to as cybersecurity risks). Such risks may not necessarily affect financial reporting, as an entity’s IT environment may also include IT applications and related data that address operational or compliance needs. It is important to note that cyber incidents usually first occur through the perimeter and internal network layers, which tend to be further removed from the IT application, database and operating systems that affect the preparation of the financial statements. Accordingly, if information about a security breach has been identified, the auditor ordinarily considers the extent to which such a breach had the potential to affect financial reporting. If financial reporting may be affected, the auditor may decide to understand, and test the related controls to determine the possible impact or scope of potential misstatements in the financial statements or may determine that the entity has provided adequate disclosures in relation to such security breach (CAS 315 Appendix 5.19).
OAG Guidance
The risk assessment considerations outlined in Cybersecurity risk assessment considerations are designed to assist in understanding, identifying and assessing the relevance and applicability of cybersecurity risks arising from the use of IT, when designing and executing procedures to audit an entity’s financial statements.
Entities may have cybersecurity risks that relate to unauthorized access to financial reporting applications, as well as data and digital/electronic assets recorded on the balance sheet, each of which may have an impact on the financial statements. Consider the following examples:
- An entity that experienced a cybersecurity attack, in which some or all of its financial reporting data was deleted. Without appropriate backup and recovery controls, the entity’s ability to report complete and accurate financial data may be impacted or the entity may not be able to meet its reporting deadlines.
- An entity that was the victim of a business email compromise whereby it received a request to change a vendor’s bank account information and remit payment for open invoices. Without vendor master data controls to validate the authenticity of the request, the entity may inaccurately relieve a liability from its books which could lead to accounts payable being understated.
- A technology entity which has experienced a cybersecurity incident that resulted in theft of a patented new technology. If this technology had a material intangible asset value recorded on the balance sheet, the entity may have an impairment event of which, without appropriate intrusion and detection controls, it may be unaware at the reporting period end date.
For financial reporting purposes, it is also important to consider the risk that costs are not accrued related to cybersecurity incidents which could include, for example, customer remediation activities, legal fees, fees related to forensic investigations and regulatory assessments.
Other cybersecurity incidents may not directly affect the financial statements. For example, in many cybersecurity breaches, the acquisition of sensitive customer information, including credit card information, is the target. Because this type of customer information is not normally recognized as an asset on an entity’s financial statements, the risk is more likely to relate to operational matters such as business interruption and damage to customer relationships which may negatively impact future operating results and cash flows. Such incidents may necessitate actions to be taken by the entity that give rise to incremental costs that need to be accrued, for example costs related to customer remediation, as well as incremental costs resulting from legal claims and regulatory actions.
Examples of cybersecurity incidents
Some additional examples of common cybersecurity incidents are provided below. Cybersecurity incidents such as these could give rise to financial statement and operational impacts similar to those already illustrated in the examples above. The nature and magnitude of impacts arising from such cybersecurity incidents will vary depending on entity specific facts and circumstances, as well as the nature of the cybersecurity incident. Therefore, we consider the potential impacts of cybersecurity incidents on an entity’s financial statements in the context of our understanding of the entity:
- A hotel chain where an elongated data breach resulted in compromise of customers’ names, travel and credit card details and other personal information (Eavesdropping attack);
- Healthcare system hacking whereby patient data was compromised (Password attack);
- Utility entity whose utility control systems were accessed by hackers (Man‑in‑the‑Middle or MitM attack); Commercial websites whose primary revenue generating service was affected by distributed denial of service attacks (DDoS attack), which are designed to make systems unavailable to intended users;
- Banks compromised in a cybersecurity attack, whereby customer information was accessed (Spyware malware);
- Data‑driven entities where hackers gained access to corporate servers and intellectual property was stolen (SQL injection attack);
- Telecommunication entities where the operating system was blocked by encrypting all archives and connected units inside the network, in an extortion scheme whereby payment was demanded in exchange for return of control (Ransomware malware);
- Entertainment and media entity encountering a security breach resulting in unauthorized acquisition of digital assets with a downstream impact to the recoverability of financial data (Spear phishing attacks).
The subsection Audit procedures related to cybersecurity places increased emphasis on consideration of the growing cybersecurity risk that entities face and provides considerations to assist in assessing whether cybersecurity may present a risk of material misstatement, including:
- Discussion of our responsibilities under the auditing standards related to risk assessment and cybersecurity;
- Matters for us to consider when executing risk assessment procedures to determine whether cybersecurity may present a risk of material misstatement;
- Conditions or events that could increase inherent risk factors, e.g., the entity uses a third‑party application that has been found to have vulnerabilities that are passed to entities if they apply a specific patch
- Risk of material misstatement at the financial statement level, e.g., a ransomware malware that blocks all access to transaction level data in both the live and back‑up environments. This would impact on every element of the financial statements
- Cybersecurity related risks arising from the use of IT, e.g., the network does not adequately prevent unauthorized users from gaining inappropriate access to information systems.
- Additional considerations to assist us in further understanding activities and controls in place at the entity to address common cybersecurity risks, including illustrative controls; and
- Actions to assess a potential cyber incident to determine the impact on our audit plan and the entity’s financial reporting.
OAG Guidance
Cybersecurity is an evolving risk to consider as part of understanding the IT environment and risk assessment activities. Our understanding establishes a frame of reference which assists us in planning our controls and substantive audit procedures. In accordance with CAS, we are required to understand the events, conditions and activities that might have a significant effect on the risks of material misstatement. Risks of material misstatement can arise from a variety of sources, including external factors, such as conditions in the entity’s industry and environment, and entity‑specific factors such as the nature of the entity and its activities.
Our understanding needs to include how the entity uses information technology so that we can assess the cybersecurity risks arising from the use of IT. This helps us to consider the reliability of financial reporting, automated controls, IT general controls (ITGCs) and the reliability of data used in the audit.
An understanding of the entity’s cybersecurity risks, its approach to IT risks, and the relevant aspects of its security architecture will be obtained as part of our procedures performed to obtain an understanding of how the entity responds to the risks arising from the use of IT, including controls subject to design and implementation evaluation. If we identify cybersecurity risks that give rise to a risk of material misstatement (due to error or fraud) to the financial statements, we need to address them in our audit plan (e.g., identify information processing controls and ITGCs and test their operating effectiveness, and/ or perform substantive testing in response to the identified risks). Note that not all cybersecurity risks will necessarily give rise to a risk of material misstatement due to fraud or error, although it is important to consider whether there are direct, or indirect impacts such as interruptions of operations, that could give rise to a risk of material misstatement. See the “Points of focus” and “cybersecurity risk exposures” tables in the section Cybersecurity risk assessment considerations and related illustrative controls for areas to consider when assessing cybersecurity risks and related controls for the entity.
Our primary focus is on IT applications and other aspects of IT that manage financial statement data, as illustrated in the chart included in the section cybersecurity risk assessment considerations—Overview that shows the typical access path to the IT environment and the programs and data. As part of understanding the entity and its IT environment, we may obtain an understanding of network security and related controls (e.g., intrusion detection) to identify cybersecurity risks of material misstatement. When considering cybersecurity risks and/or cybersecurity incidents we may determine there are indications of an increased risk of unauthorized access at the network layer. Cybersecurity risks could impact on more than one ITGC domain or be pervasive across the entity.
It is important to note that cybersecurity incidents usually first occur through the perimeter and internal network layers, as illustrated by the chart in the section Access to programs and data, which tend to be further removed from financial applications on which we typically focus our attention during our audits.
Engagement leaders need to be sufficiently involved in identifying cybersecurity risks, determining the possible impact or scope of potential misstatements in the financial statements and evaluating whether cybersecurity risks could lead to risks of material misstatement. Developing the audit strategy relies upon the engagement leader and team manager understanding the entity and its industry, reviewing management’s risk assessment and considering other risks, all of which are needed to enable a robust risk assessment.
It is important for engagement leaders to be engaged in and plan for appropriate internal and external discussions regarding the risk assessment process and our approach to cybersecurity as an enterprise‑wide consideration rather than just an information technology issue. Because cybersecurity is an important enterprise‑wide risk that most entity’s management teams, audit committees and boards will typically have considered, our risk assessment may be enhanced by engaging with them on this topic during the planning phase of the audit. Consider engaging IT Audit or other cybersecurity subject matter experts who have the requisite experience to help evaluate cybersecurity risks in complex environments and/or when cybersecurity incidents have occurred.
OAG Guidance
The objective of the cybersecurity risk assessment areas and points of focus, included in the table below, is to help us gather information, as part of performing risk assessment procedures, needed to determine the nature, timing and extent of further procedures to be performed as part of the audit. Consider engaging IT Audit when performing risk assessment procedures in the areas outlined in this section. In highly complex environments we may also involve cybersecurity subject matter experts.
The areas and points of focus in the table below also may assist us in evaluating whether risks related to cybersecurity give rise to a risk of material misstatement and, ultimately, to identify any related impact to the risk assessment and on the audit strategy and plan. See the section Identify risks arising from the use of IT for further guidance on identifying risks arising from the use of IT. Based on the considerations below and any other relevant considerations, we use professional judgment to determine the impact of cybersecurity on our risk assessment and planned audit procedures. Based on our assessment, we determine if changes are needed to the nature, timing and extent of planned procedures and if:
- Any controls need to be tested as part of our audit; and/or
- Any additional substantive procedures need to be performed in response to an assessed risk.
If we identify any significant risks related to cybersecurity, we need to communicate those in accordance with CAS 260 and OAG Audit 2214.
| Ref | Area | Points of focus* |
|---|---|---|
| 1 | Risk Assessment |
|
| 2 | Roles and Responsibilities |
|
| 3 | Safeguarding of Assets |
|
| 4 | Security Breaches |
|
| 5 | Disclosures to Entity’s Stakeholders |
Examples affecting financial reporting impacts include:
|
*Points of focus related to assessing risks regarding access to customer information, privacy and physical security are specifically excluded from this risk assessment as these are normally not related to risks of material misstatements of the financial statements.
The following table includes common cybersecurity risk exposures. Consider these common exposures as part of risk assessment procedures and document our consideration in the relevant planning procedure Understand cybersecurity risk related to the audit. To the extent any of these cybersecurity risks represent a risk of material misstatement to the financial statements, consider the impact on our audit plan, including adjusting our controls testing plan as necessary.
| Area | Risk Considerations | Control Considerations | Illustrative Controls |
|---|---|---|---|
| Entity level Information and Communication | Spoofed or compromised electronic communications from persons purporting to be company executives or vendors with instructions to transfer funds resulting in payments that are not appropriately accounted for |
|
The entity maintains and periodically reviews policies and procedures pertaining to cybersecurity risk management, including information and communication mechanisms for ensuring potential cyber schemes are communicated to finance management. On a periodic basis, employees complete a security awareness training program that includes cybersecurity risk management practices (e.g., phishing campaigns). |
| Vendor setup/modification | Certain cyber schemes have been identified in which changes to bank account or other critical vendor information have been requested through email phishing scams by individuals purporting to be authorized vendor personnel. Entities have inappropriately dispersed funds to these individuals and therefore inappropriately reduced the liability owed to the actual vendor, resulting in an impact to the financial statements (i.e., loss of cash and related expense as well as the need to re‑establish the vendor accrual) |
|
The entity performs a periodic risk assessment of critical vendor information. The setup and modification of critical vendor information (e.g., bank account information) is authorized prior to update in the vendor management system (including callback or other verification procedures). |
| Electronic transfers of funds (may also be known as wire transfers, electronic funds transfers) | Similar to vendor changes noted above, cyber schemes pertaining to fraudulent requests for wire transfers have been made relating to business transactions and vendor payments, as well as fraudulent requests appearing to come from financial institutions requesting disbursement from customer asset accounts |
|
The entity has implemented and periodically reviews policies and procedures pertaining to cash and wire transfers that ensure all remittances are authorized by independent and appropriate personnel. |
| Intrusion prevention/ detection and monitoring | Intrusion attacks (e.g., ransomware) may occur, preventing the entity from accessing its critical infrastructure or data |
|
The entity periodically reviews intrusion prevention and/or detection tools to ensure tools are configured to monitor financially critical assets. Incidents pertaining to potential security threats are identified by intrusion prevention and/or detection tools and managed to remediate in a timely manner. |
| Patch management |
Cyber and ransomware attacks exploiting known security vulnerabilities resulting in the manipulation or the destruction of data that impacts the financial statements or affects system availability impacting timely financial reporting. Known security vulnerabilities are exploited in cyber attacks enabling many of the exposure areas described above to be exploited. Exploitations of known security vulnerabilities may be caused by unapplied patches. |
|
The entity maintains and periodically reviews policies and procedures pertaining to patch management. Patches related to potential security vulnerabilities are implemented on a timely basis to respond to identified vulnerabilities. Periodic scans are performed to identify potential vulnerabilities attributable to missed or unapplied security patches. |
| Backup and Recovery | Lack of effective backup and recovery procedures resulting in cybersecurity incidents that render systems inoperable (e.g., ransomware attacks), which may threaten the ability of the entity to prepare the financial statements or file them on a timely basis |
|
The entity periodically reviews recovery time objectives for financially critical systems needed to support timely financial reporting. The entity periodically tests backup and recovery processes to ensure financially critical systems needed to support timely financial reporting can be recovered in accordance with recovery time objectives and recovery point objectives in the event of a cyber attack. |
OAG Guidance
Cybersecurity incidents could have an impact on our risk assessment. Depending on the type of incident, and the entity’s response, this could impact on a small area of the audit, for example, requiring a more detailed walkthrough of the entity’s intrusion detection controls). Some cybersecurity incidents could be more pervasive and impact across the financial transactions, for example, if there is a ransomware attack which threatens the ability of the entity to prepare the financial statement. The following guidance may be used to help facilitate discussions with audit clients when we are notified of potential data corruption, security breach(es) or other security incidents:
| Step | Engagement Team Actions |
|---|---|
| 1 |
Understand the what, when, where, and how of the incident
|
| 2 |
Request information from client
|
| 3 |
Analyze information received, review findings and determine financial reporting impact (e.g., systems impacted, potential control deficiencies)
|
| 4 |
Document audit response (if applicable)
|
As mentioned in the step 1, the following questions for client discussion may assist us in understanding the incident:
| Incident Phase | Considerations |
|---|---|
| Detect |
|
| Assess |
|
| Respond |
|
| Recover |
|