Annual Audit Manual
COPYRIGHT NOTICE — This document is intended for internal use. It cannot be distributed to or reproduced by third parties without prior written permission from the Copyright Coordinator for the Office of the Auditor General of Canada. This includes email, fax, mail and hand delivery, or use of any other method of distribution or reproduction. CPA Canada Handbook sections and excerpts are reproduced herein for your non-commercial use with the permission of The Chartered Professional Accountants of Canada (“CPA Canada”). These may not be modified, copied or distributed in any form as this would infringe CPA Canada’s copyright. Reproduced, with permission, from the CPA Canada Handbook, The Chartered Professional Accountants of Canada, Toronto, Canada.
7052 External confirmation procedures
Jun-2021
In This Section
Types of information subject to confirmation
Design and execution of external confirmations
Use of positive or negative confirmations
Responding to management’s request not to send confirmations
Overview
This topic explains:
- Types of information subject to confirmation
- The requirements relating to design and execution of external confirmations
- Follow-up requests
- Use of positive or negative confirmations
- Responding to management’s request not to send a confirmation
- Timing of external confirmation procedures
CAS Requirement
When using external confirmation procedures, the auditor shall maintain control over external confirmation requests, including:
(a) Determining the information to be confirmed or requested (CAS 505.7(a))
CAS Guidance
External confirmation procedures frequently are performed to confirm or request information regarding account balances and their elements. They may also be used to confirm terms of agreements, contracts, or transactions between an entity and other parties, or to confirm the absence of certain conditions, such as a "side agreement" (CAS 505.A1).
External confirmation procedures frequently are relevant when addressing assertions associated with account balances and their elements, but need not be restricted to these items. For example, the auditor may request external confirmation of the terms of agreements, contracts or transactions between an entity and other parties. External confirmation procedures also may be performed to obtain audit evidence about the absence of certain conditions. For example, a request may specifically seek confirmation that no 'side agreement' exists that may be relevant to an entity's revenue cut‑off assertion. Other situations where external confirmation procedures may provide relevant audit evidence in responding to assessed risks of material misstatement include (CAS 330.A50):
-
Bank balances and other information relevant to banking relationships
-
Accounts receivable balances and terms
-
Inventories held by third parties at bonded warehouses for processing or on consignment
-
Property title deeds held by lawyers or financiers for safe custody or as security
-
Investments held for safekeeping by third parties, or purchased from stockbrokers but not delivered at the balance sheet date
-
Amounts due to lenders, including relevant terms of repayment and restrictive covenants
-
Accounts payable balances and terms
OAG Guidance
Other examples of situations where external confirmations may be used include the following:
- Contract terms and collateral
- Investments in debt and equity securities
- Share information
CAS Requirement
When using external confirmation procedures, the auditor shall maintain control over external confirmation requests, including: (CAS 505.7):
(b) Selecting the appropriate confirming party
(c) Designing the confirmation requests, including determining that requests are properly addressed and contain return information for responses to be sent directly to the auditor
(d) Sending the requests, including follow-up requests when applicable, to the confirming party
CAS Guidance
Responses to confirmation requests provide more relevant and reliable audit evidence when confirmation requests are sent to a confirming party the auditor believes is knowledgeable about the information to be confirmed. For example, a financial institution official who is knowledgeable about the transactions or arrangements for which confirmation is requested may be the most appropriate person at the financial institution from whom to request confirmation (CAS 505.A2).
The design of a confirmation request may directly affect the confirmation response rate, and the reliability and the nature of the audit evidence obtained from responses (CAS 505.A3).
Factors to consider when designing confirmation requests include (CAS 505.A4):
-
The assertions being addressed.
-
Specific identified risks of material misstatement, including fraud risks.
-
The layout and presentation of the confirmation request.
-
Prior experience on the audit or similar engagements.
-
The method of communication (for example, in paper form, or by electronic or other medium).
-
Management's authorization or encouragement to the confirming parties to respond to the auditor. Confirming parties may only be willing to respond to a confirmation request containing management's authorization.
-
The ability of the intended confirming party to confirm or provide the requested information (for example, individual invoice amount versus total balance).
Determining that requests are properly addressed includes testing the validity of some or all of the addresses on confirmation requests before they are sent out (CAS 505.A6).
OAG Guidance
Maintaining control of the confirmation process
We need to maintain control over the entire external confirmation process to minimize the risk of requests and responses being intercepted and altered. We need to send confirmation requests directly to and receive returned confirmations directly from the confirming parties and not allow the client or any party that is not part of the engagement team to send or receive them on our behalf. Maintaining control of the confirmation request process generally includes the following core elements:
-
selecting appropriate confirming party;
-
providing a format for the confirmation request that outlines the information to be requested;
-
testing the validity of the address details provided;
-
sending the confirmations directly to the confirming party;
-
where sending through the postal mail service, providing a self‑addressed envelope with the confirmation requests to enable the confirming party to return the confirmation directly to us; and
-
performing additional follow-up procedures in circumstances where the confirmation request is returned to the entity’s premises or received via email and subsequently provided to the engagement team (e.g., requesting the confirming party to send a new response directly to us).
This guidance details the considerations relevant to maintaining control of the external confirmation process, as required by CAS 505, and obtaining relevant and reliable substantive audit evidence. The judgments we make regarding these considerations will vary depending upon engagement specific facts and circumstances, but typically the judgments are made as part of three key elements of the external confirmation process, as follows:
-
Selecting the appropriate confirming party (see 'Selecting the appropriate confirming party' section below)
-
Testing the validity of the mailing address to be used to send the confirmation request to (see 'Testing the validity of addresses on confirmation requests' section below)
-
Assessing the reliability of the confirmation response, including considering the need to perform additional procedures based on factors such as the method of receiving the confirmation responses (see OAG Audit 7053)
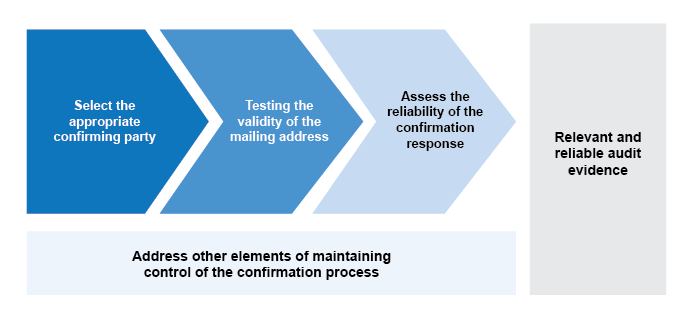
Selecting the appropriate confirming party
As noted in CAS 505.A2, responses to confirmation requests provide more relevant and reliable audit evidence when confirmation requests are sent to a confirming party we believe is knowledgeable about the information to be confirmed.
Within certain entities, confirmation requests may be completed by one person or a limited number of people. For example, a confirming party may have a policy that all confirmation requests are to be completed by an accounts payable manager or supervisor rather than a group of accounts payable clerks. Care needs to be taken to address the confirmation request to the individual (or individuals) who is knowledgeable about the information to be confirmed and who is authorized to complete the confirmation on behalf of the confirming party's entity (in the example above that would be the manager or supervisor, rather than one of the clerks).
Although we are required to maintain control over the external confirmation requests, including remaining responsible for selecting the appropriate confirming party, in practice we may require assistance from client management to obtain information needed. For example, we may need management to provide us with information when obtaining an understanding of the position and responsibilities of the confirming party entity official to whom we are proposing to send the request. We also consider whether our prior experience on the audit or on similar engagements assists us in selecting the appropriate confirming party.
If we encounter difficulties in identifying the appropriate confirming party or if we have questions about the appropriateness of the confirming party suggested by client management, we need to perform additional procedures. For example, reviewing the confirming entity's corporate website to determine if an appropriate confirming party is identified or calling the proposed confirming party directly to determine whether they are the appropriate party (the telephone inquiry could also be used to test the validity of the address to which the confirmation request is to be sent). We document the results of any such additional procedures performed in the workpapers.
Appropriate conforming party—fiduciary relationships
There may be situations where the entity we are auditing engages another party to manage assets on their behalf. For example, the entity may engage a third party such as an investment manager to manage an asset portfolio that belongs to the entity. In situations such as this it is important that we understand the fiduciary arrangement, including the business rationale and the resulting responsibilities, rights and obligations between the parties to understand the risks arising from this fiduciary relationship. For confirmation purposes this is important for selecting the right confirming party because it can impact the reliability and persuasiveness of the audit evidence we intend to obtain through confirmation.
To select the appropriate confirming party when multiple parties form part of a fiduciary arrangement, we need to consider which party is best positioned to be knowledgeable about the information we seek to confirm and assertions we plan to address. For example, if cash or other assets are held directly by a trustee, it would be appropriate to obtain a confirmation from the trustee. However, in situations where a trustee engages other parties (e.g., investment managers, custodians) to hold the assets, it would be more appropriate to obtain the confirmation from those other parties. Typically, the party that has custody of the assets is the appropriate confirming party to confirm completeness and existence of the assets and the party that is responsible for managing the assets (e.g, investment managers) would be best placed to confirm valuation of the assets. However, the appropriate conforming party for the existence, completeness and valuation assertions may be different depending on the responsibilities, rights and obligations of the parties to fiduciary arrangement. If we obtain confirmations addressing relevant assertions about the same assets from different parties (e.g., custodian for completeness and existence and investment manager for valuation), we need to compare the information underlying each confirmation to verify that they agree and reconcile (e.g., the individual asset descriptions and quantities included in the investment manager's confirmation of asset values agrees to the asset descriptions and quantities confirmed by the custodian) and address any identified differences, as appropriate.
As with other third-party confirmations, we need to maintain control over the confirmation process and obtain confirmations directly from the confirming parties. In some cases, the entity or the trustee may need to communicate with the confirming parties to authorize them to provide information directly to us. For example, if the trustee engages a bank to act as a custodian, information protection regulations may prohibit the bank from sharing information with us without consent from the trustee or entity we audit. To facilitate our control of the confirmation process, in this example, the entity's (or trustee's) authorization communication to the bank needs to be clear that the authorization communication is not a confirmation request and the entity's auditor will be sending a confirmation request directly to the confirming party.
An understanding of the fiduciary arrangement may also be important when considering the appropriate confirming party and the persuasiveness of evidence the confirmation provides. For example, if a trustee receives fees based on the value of the assets they manage on behalf of the entity we are auditing, this could indicate an incentive for the trustee to overstate the value of assets, in which case we consider whether there is another appropriate confirming party and/or we may need to obtain additional evidence about the existence and valuation of the assets confirmed by the trustee. Examples of procedures that we might consider include, but are not limited to, obtaining a service organization auditor's report for an investment manager to obtain evidence on their controls over existence and valuation of investments, and/or verifying the investment valuation by independently obtaining evidence over the market value of quoted investments.
Determining the method for sending external confirmation requests
When sending external confirmation requests, we consider the most appropriate method, taking into account the engagement specific circumstances, including identified material fraud risks and susceptibility to interception and/or alteration of the confirmation. Some considerations when selecting the appropriate method include, but are not limited to, the following:
-
Sending a hardcopy request to the confirming party's physical mailing address through postal mail service, with an expectation of receiving an original hardcopy response through the postal mail service
- Any form of confirmation is subject to a risk of interception and alteration. However, typically this risk is lower for hard copy confirmations than for electronic or facsimile responses, because an original hardcopy confirmation response provides the most effective format for considering whether there are indicators that the confirmation may not be reliable (e.g., where official stamps, seals or chops are used by the confirming party). Irrespective of the format of receipt, we are always required to consider whether there is an indication that external confirmations received may not be reliable as described in OAG Audit 7053.
- When using hardcopy confirmations, the external confirmation plan needs to allow sufficient time for the request and any follow‑up requests to be sent, and response received, through the postal mail system.
-
Sending a request electronically using a secure Assurance Software Tool designed to support the external confirmation process, with an expectation of receiving a response directly through the tool
- Tools that provide a secure environment for sending and receiving confirmations from confirming parties, mitigate reliability risks related to proof of origin for confirmation responses.
- The secure environment also mitigates the heightened risks related to interception/alteration of electronic confirmation responses, subject to testing the validity of the confirming party's email address used to invite the confirming party to respond to the confirmation. Where such a tool is used, additional procedures to address proof of origin, interception and alteration risks may not be necessary, although we are always required to consider whether there are indications that external confirmations received may not be reliable as described in OAG Audit 7053.
- In light of cybersecurity risks such as phishing schemes, confirming parties may be reluctant to respond to the automated email inviting them to access tools to respond to the confirmation. Consider whether steps can be taken to increase the confirming party's confidence without compromising our control of the confirmation process (e.g., client management sending a letter or email to the confirming party advising them that they should expect an email confirmation request with an image of the email format and sender details).
-
Request sent using a OAG email account, with an expectation of receiving a response in a OAG email account
- Responses received electronically involve risks as to reliability because proof of origin and authority of the respondent may be difficult to establish, and interception and alterations may be difficult to detect. When sending or receiving confirmations by email rather than using a secured tool designed to support the external confirmation process, these risks are not mitigated by a secure environment between us and the confirming party. As a result, when a response is received in an OAG email account, we need to perform additional procedures to determine the authenticity of the confirming party as described in OAG Audit 7053.
- Some data protection laws and regulations include protections for client data that may need to be adhered to when sending and receiving external confirmations using email. Adherence to data protection requirements may impact, for example, whether client consent to release information is needed, the form and content of the confirmation request and/or whether the confirmation request or response need to be sent using encrypted emails.
If a confirmation request is sent with an expectation of receiving an original hardcopy response or a response using an Assurance Software Tool designed to support the external confirmation process, but instead the confirming party sends the confirmation response to an OAG email account, then upon receipt of the confirmation our considerations related to determining the authenticity of the confirming party are the same as if we had originally sent the request expecting to receive an email response (i.e., we need to perform additional procedures to determine the authenticity of the confirming party as described in OAG Audit 7053.
Test the validity of addresses on confirmation requests
As noted in CAS 505.A6, we need to test the validity of some or all of the addresses on confirmation requests before they are sent out. We may use a variety of approaches in performing procedures to test the validity of addresses, including referring to third party sources such as confirming party's website to determine whether the confirming party's physical address or the domain portion of their email address (e.g., abc.com) is consistent with the address details found in the "Contact us" or "About us" (or equivalent) section of the website. When performing this procedure, we apply professional skepticism in evaluating whether the website appears to be a legitimate corporate website of the confirming party. The nature and extent of our procedures depend on the risks associated with the particular type of confirmation or address. For example, a confirmation addressing a higher‑risk assertion or a confirmation party address that is not typical of similar confirming parties (e.g., residential address) may necessitate different or more extensive procedures (such as testing the validity of all addresses on confirmation requests by referring to third party sources or calling the confirming party directly) to determine that the request is directed to the intended recipient.
Sending confirmation requests to email addresses – Additional considerations
As noted in CAS 505.A12, sending confirmation requests to email addresses with a view to also receiving a response via email introduces risks as to reliability because proof of origin and authority of the respondent may be difficult to establish, and alterations may be difficult to detect. To help mitigate these risks, where electronic requests are to be sent, consider using a secure Assurance Software Tool designed to support the external confirmation process by creating a secure environment for receiving confirmations from third parties. When such a tool is not available, and confirmation requests are to be sent by email, consider the nature of the confirming party's email address to be used when determining the nature and extent of address validation procedures, including as follows:
-
Individual corporate email addresses are associated with the intended confirming party's entity and are expected to be accessed and utilized by a single individual within an entity (e.g., john.doe@oag-bvg.gc.ca). As risks, such as those related to proof of origin, associated with this type of email address are normally considered lower than for the other types of email addresses described below, we apply professional judgment to decide whether to test the validity of some of these types of addresses or whether to test all of them.
-
Group-corporate email addresses use a single email address associated with the confirming party's entity that can be accessed and utilized by multiple individuals employed within a function or department of the entity (e.g., accountspayable@oag-bvg.gc.ca). We test the validity of group‑corporate email addresses in two steps:
- We perform procedures over the validity of all group-corporate email domains prior to sending the confirmation requests. For example, by referring to third party sources such as the confirming party's website to determine whether the domain portion of the confirming party's email address (e.g., abc.com) is consistent with the address details found in the "Contact us" or "About us" (or equivalent) section of the website; and
- Following receipt of the confirmation response, we perform the same procedures we would need to perform for "other than original" confirmation responses (See OAG Audit 7053). These procedures include, considering the authenticity of the confirming party and the information included in the confirmation response and either documenting in the workpaper our reasons for being satisfied or, where there is uncertainty, verifying the electronic response by calling the confirming party and documenting the communication in the workpaper.
-
Non-corporate email addresses use email domains that are not owned by the confirming party's entity, such as those available from a freeware domain (e.g., john.doe@gmail.com) or a pay‑to‑use email domain that is not owned by the confirming party. Because there may be heightened risk related to proof of origin associated with receiving confirmation responses from this type of email address, for all non‑corporate email addresses we perform additional validation procedures, contacting the confirming party by telephone in an attempt to verify that the email address is an appropriate destination for our confirmation request.
Sending confirmation requests to Post Office boxes—Additional considerations
The confirming party's address on the confirmation request may be a post office (PO) box. Typically, we test the validity of all PO box addresses in the same manner as any physical address (e.g., referring to third party sources such as the "Contact us" or "About us" (or equivalent) section of the website confirming party's website). However, in some cases there may not be a source available to the general public to verify that the PO box is the appropriate address for the confirming party. In these instances, we may use procedures such as determining the post office location in which the PO box is located and comparing its proximity to the confirming party's and the client's physical address for consistency and reasonableness. We may also contact the confirming party in a manner similar to that followed when a response is received electronically. In instances where multiple confirmation requests are addressed to PO boxes, we may compare the post office location(s) of the PO boxes looking for any patterns of PO box addresses or their physical locations that might suggest the address is not valid.
|
Audit Tip Working collaboratively with the client on the confirmation process in a timely manner will help to minimize the level of effort required for follow‑up as the report release date approaches. |
CAS Guidance
The auditor may send an additional confirmation request when a reply to a previous request has not been received within a reasonable time. For example, the auditor may, having re‑verified the accuracy of the original address, send an additional or follow‑up request (CAS 505.A7).
CAS Requirement
Negative confirmations provide less persuasive audit evidence than positive confirmations. Accordingly, the auditor shall not use negative confirmation requests as the sole substantive audit procedure to address an assessed risk of material misstatement at the assertion level unless all of the following are present (CAS 505.15):
(a) The auditor has assessed the risk of material misstatement as low and has obtained sufficient appropriate audit evidence regarding the operating effectiveness of controls relevant to the assertion;
(b) The population of items subject to negative confirmation procedures comprises a large number of small, homogeneous, account balances, transactions or conditions;
(c) A very low exception rate is expected; and
(d) The auditor is not aware of circumstances or conditions that would cause recipients of negative confirmation requests to disregard such requests.
CAS Guidance
A positive external confirmation request asks the confirming party to reply to the auditor in all cases, either by indicating the confirming party's agreement with the given information, or by asking the confirming party to provide information. A response to a positive confirmation request ordinarily is expected to provide reliable audit evidence. There is a risk, however, that a confirming party may reply to the confirmation request without verifying that the information is correct. The auditor may reduce this risk by using positive confirmation requests that do not state the amount (or other information) on the confirmation request, and ask the confirming party to fill in the amount or furnish other information. On the other hand, use of this type of "blank" confirmation request may result in lower response rates because additional effort is required of the confirming parties (CAS 505.A5).
The failure to receive a response to a negative confirmation request does not explicitly indicate receipt by the intended confirming party of the confirmation request or verification of the accuracy of the information contained in the request. Accordingly, a failure of a confirming party to respond to a negative confirmation request provides significantly less persuasive audit evidence than does a response to a positive confirmation request. Confirming parties also may be more likely to respond indicating their disagreement with a confirmation request when the information in the request is not in their favor, and less likely to respond otherwise. For example, holders of bank deposit accounts may be more likely to respond if they believe that the balance in their account is understated in the confirmation request, but may be less likely to respond when they believe the balance is overstated. Therefore, sending negative confirmation requests to holders of bank deposit accounts may be a useful procedure in considering whether such balances may be understated, but is unlikely to be effective if the auditor is seeking evidence regarding overstatement (CAS 505.A23).
CAS Requirement
If management refuses to allow the auditor to send a confirmation request, the auditor shall (CAS 505.8):
(a) Inquire as to management's reasons for the refusal, and seek audit evidence as to their validity and reasonableness;
(b) Evaluate the implications of management's refusal on the auditor's assessment of the relevant risks of material misstatement, including the risk of fraud, and on the nature, timing and extent of other audit procedures; and
(c) Perform alternative audit procedures designed to obtain relevant and reliable audit evidence.
If the auditor concludes that management's refusal to allow the auditor to send a confirmation request is unreasonable, or the auditor is unable to obtain relevant and reliable audit evidence from alternative audit procedures, the auditor shall communicate with those charged with governance in accordance with CAS 260. The auditor also shall determine the implications for the audit and the auditor's opinion in accordance with CAS 705 (CAS 505.9).
CAS Guidance
A refusal by management to allow the auditor to send a confirmation request is a limitation on the audit evidence the auditor may wish to obtain. The auditor is therefore required to inquire as to the reasons for the limitation. A common reason advanced is the existence of a legal dispute or ongoing negotiation with the intended confirming party, the resolution of which may be affected by an untimely confirmation request. The auditor is required to seek audit evidence as to the validity and reasonableness of the reasons because of the risk that management may be attempting to deny the auditor access to audit evidence that may reveal fraud or error (CAS 505.A8).
The auditor may conclude from the evaluation in paragraph 8(b) that it would be appropriate to revise the assessment of the risks of material misstatement at the assertion level and modify planned audit procedures in accordance with CAS 315. For example, if management's request to not confirm is unreasonable, this may indicate a fraud risk factor that requires evaluation in accordance with CAS 240 (CAS 505.A9).
The alternative audit procedures performed may be similar to those appropriate for a non‑response as set out in paragraphs A18‑A19 of CAS 505. Such procedures also would take account of the results of the auditor's evaluation in paragraph 8(b) of this CAS (CAS 505.A10).
OAG Guidance
Our conclusions with regards to management refusal to allow a confirmation request to be sent are documented in the related workpaper.
If we conclude management’s refusal may indicate fraud risk, reflect that conclusion in the related workpaper on fraud risk assessment as appropriate. If we revise our assessment of risk as a result, consider whether changes are necessary to the nature, timing and extent of procedures to address the risk.
Consider if these circumstances are so significant as to require discussion with the engagement leader and treatment as a significant matter, and communication to those charged with governance.
In circumstances where we are unable to obtain sufficient appropriate audit evidence through use of alternative procedures to address the risk and assertions the confirmation request was designed to test, this may give rise to a limitation of scope and have implications for our audit opinion. For further guidance with respect to scope limitations see OAG Audit 8013.
Related guidance
See guidance on communicating with those charged with governance at OAG Audit 2210.
See guidance on action on discovery of possible fraud at OAG Audit 5506.
OAG Guidance
When we use confirmations as at a date prior to the balance sheet to obtain evidence to support a financial statement assertion, we need to obtain sufficient appropriate audit evidence that transactions relevant to the assertion in the intervening period have not been materially misstated. As with all types of interim work, we consider the need to obtain further audit evidence relating to the remainder of the period.
Related guidance
See guidance on substantive procedures prior to balance sheet date at OAG Audit 7015.